Quantum computing’s potential is often compromised by various forms of noise or errors, including crosstalk. This article explores the impact of crosstalk noise in a shared quantum computing environment, such as cloud-based services. Researchers from The University of Melbourne and Quantum Systems Data61 CSIRO in Australia have analyzed crosstalk noise on IBM Quantum computers and developed an enhanced simulation model. They also proposed three crosstalk attack mitigation strategies: circuit separation, qubit allocation optimization via reinforcement learning, and the use of spectator qubits. The research highlights the significant ecurity concern crosstalk attacks pose for quantum computing, especially in shared environments.
What is the Impact of Crosstalk Attacks on Quantum Computing?
Quantum computing has the potential to solve problems that are currently unsolvable on classical computers. However, the accuracy of quantum computers is often compromised by various forms of noise or errors, such as leakage, crosstalk, dephasing, and amplitude damping. This article focuses on the impact of crosstalk noise in a shared quantum computing environment, where access to quantum computers is primarily through cloud-based services.
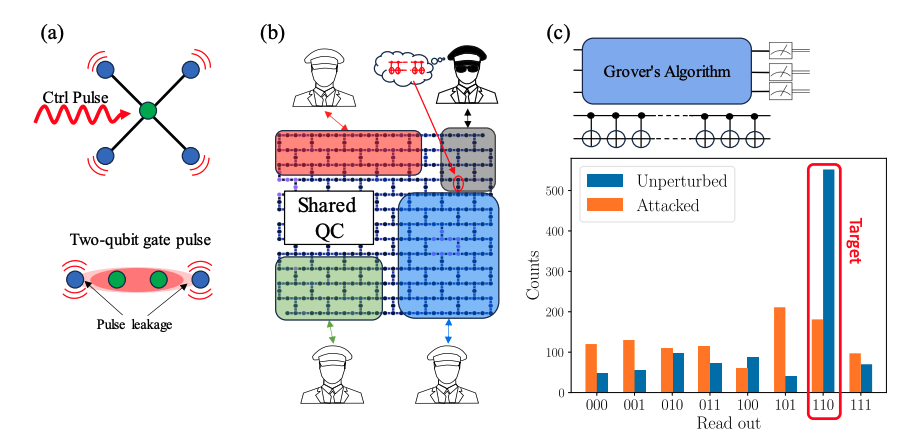
Crosstalk noise is a significant source of errors on quantum hardware, such as IBM quantum computers. It can be exploited by an adversary to disrupt quantum computations on nearby qubits, even designing quantum circuits to purposely lead to incorrect answers. This makes crosstalk-based attacks a viable threat to quantum computing in a shared environment.
How is Crosstalk Noise Analyzed and Simulated?
The researchers from the School of Physics at The University of Melbourne and Quantum Systems Data61 CSIRO in Australia analyzed the extent and characteristics of crosstalk noise through tomography conducted on IBM Quantum computers. This led to the development of an enhanced crosstalk simulation model.
The simulation model was benchmarked against IBM hardware to assess the impact of crosstalk attacks. The researchers also developed strategies for mitigating crosstalk effects. Through a systematic set of simulations, they assessed the effectiveness of three crosstalk attack mitigation strategies.
What are the Crosstalk Attack Mitigation Strategies?
The three crosstalk attack mitigation strategies are circuit separation, qubit allocation optimization via reinforcement learning, and the use of spectator qubits. All three strategies have been shown to overcome crosstalk attacks with varying degrees of success and help secure quantum computing in a shared platform.
Circuit separation involves using unused buffer qubits to distance the circuits from each other. Qubit allocation optimization via reinforcement learning is a more complex strategy that involves optimizing the allocation of qubits to minimize the impact of crosstalk noise. The use of spectator qubits involves using additional qubits that do not participate in the computation but help mitigate the effects of crosstalk noise.
How is Crosstalk Noise Different from Other Types of Noise?
Crosstalk noise is different from other types of noise in quantum computers in that it arises from the connectivity of qubits, which is essential for executing multi-qubit gates. This connectivity can lead to unwanted correlated dynamics, resulting in crosstalk noise. This type of noise results in a decline in quantum coherence and the introduction of errors in quantum computations.
Crosstalk noise is also different from malware-based attacks on conventional computers. It is inherent in the actual physics of the operation of the quantum computer, and this kind of attack vector is not possible in conventional computers. Therefore, defending against these attacks requires strategies in addition to normal security procedures.
What are the Implications of Crosstalk Attacks for Quantum Computing Security?
The potential for crosstalk attacks poses a significant security concern for quantum computing, especially in a shared environment where multiple users are executing circuits simultaneously. An adversary could craft an algorithm that interferes with nearby normal operations, causing programs to fail, provide faulty results, or leak information.
Despite the potential security implications of crosstalk attacks on quantum processors, there is currently a lack of quantitative modeling and practical mitigation strategies for real devices. The research presented in this article addresses this gap by characterizing crosstalk noise on an IBM device and presenting three techniques to detect and mitigate the effects of a crosstalk attack on a circuit.
“Crosstalk Attacks and Defence in a Shared Quantum Computing Environment” is an article authored by Benjamin Harper, Behnam Tonekaboni, Bahar Goldozian, M. E. Sevior, and Muhammad Usman. The article was published on February 5, 2024, and is available on arXiv, a repository of electronic preprints approved for publication after moderation, hosted by Cornell University. The article discusses the potential threats and defensive measures in a shared quantum computing environment. The full article can be accessed via its DOI: 10.48550/arxiv.2402.02753.