Post-Quantum Cryptography (PQC) is a system secure against both quantum and classical computers, developed to counter the potential threat of quantum computers breaking current cryptographic systems. A course in PQC has been launched by Thomas J Borrelli, Monika Polak, and Stanisław Radziszowski from the Rochester Institute of Technology and the University of Rochester. The course covers the PQC algorithm design process, the impact of quantum computing, and the development of quantum-resistant schemes. The course, first offered in Spring 2022, is attracting students interested in the future of cryptography and cybersecurity.
What is Post-Quantum Cryptography and Why is it Important?
Post-Quantum Cryptography (PQC) refers to cryptographic systems that are secure against both quantum and classical computers. These systems can be achieved through classical, non-quantum means. The security of many commonly used cryptographic protocols, especially public-key cryptosystems, would be compromised if general-purpose, large-scale, fault-tolerant quantum computers become a reality. This is because quantum computers have the potential to solve certain mathematical problems much more efficiently than classical computers, which could break many of the cryptographic systems currently in use.
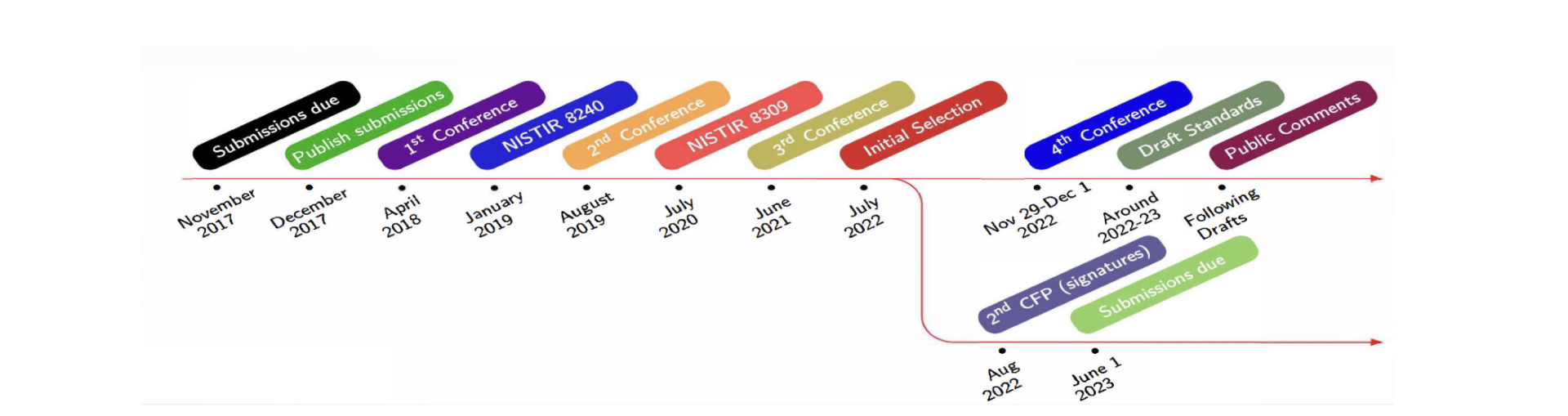
The development and launch of a course in PQC is therefore of great importance. This is due to the progress in the design of quantum computers and the ongoing National Institute of Standards and Technology (NIST) process to develop post-quantum cryptographic systems. The course is designed to cover the consequences of developments in quantum computing, the threats of quantum computing to currently used cryptographic schemes, and how to mitigate those threats by developing quantum-resistant schemes.
Who are the Key Players in Post-Quantum Cryptography?
The course was developed and launched by Thomas J Borrelli, Monika Polak, and Stanisław Radziszowski from the Department of Computer Science at the Rochester Institute of Technology and the University of Rochester. The course was first offered as an MS-level graduate course, also open to upper-level undergraduates, in Spring 2022 and followed with the second offering in Spring 2023. The course is attracting students interested in the future of cryptography and computing security/cybersecurity.
What Does the Post-Quantum Cryptography Course Cover?
The course covers the PQC algorithm design process, the consequences of quantum computing, some computationally hard problems, and then discusses selected proposals for post-quantum cryptosystems designed to be resistant to known classical and quantum attacks. Three main types of such designs include lattice-based, code-based, and hash-based schemes. These three types are used both for key encapsulation methods (KEM) and digital signatures (DS), and more generally for encryption and authentication.
How is the Post-Quantum Cryptography Course Evaluated?
In the course, the instructors reflect on what did or didn’t work and how they improved the course in the second run. They provide grade distribution and SmartEvals data. They also discuss the challenges faced in delivering the course. The paper ends with conclusions and future work in the field of post-quantum cryptography.
What is the Future of Post-Quantum Cryptography?
Quantum computing has been a topic of interest since the early 1980s. In recent years, progress in this area has been slow but steady and consistent. However, there are many indications that this progress has accelerated significantly, which in turn greatly increased attention of cryptographers to post-quantum cryptography. This attention quickly extended to the much broader cybersecurity community. Despite some setbacks, significant progress is being made. If progress continues in this fashion, as seems likely, many of the commonly-used cryptographic systems could be compromised, making the study and development of post-quantum cryptographic systems of utmost importance.
Publication details: “Designing and Delivering a Post-Quantum Cryptography Course”
Publication Date: 2024-03-07
Authors: Thomas J. Borrelli, Maurice V. Polak and Stanisław Radziszowski
Source:
DOI: https://doi.org/10.1145/3626252.3630823