Quantum computing’s rise in popularity has led to a new security threat: power trace attacks. These attacks use power traces to steal quantum circuit secrets by reverse engineering the control pulses sent to quantum computers. Two types of single trace attacks have been identified: per-channel and total power attacks. The former uses per-channel measurements for a brute-force attack to reconstruct quantum circuits, while the latter uses Mixed-Integer Linear Programming optimization. The research shows that these attacks can accurately steal quantum circuit secrets, highlighting the need for new security measures, especially as quantum computing becomes more accessible.
What is the Threat to Quantum Circuits from Power Trace Attacks?
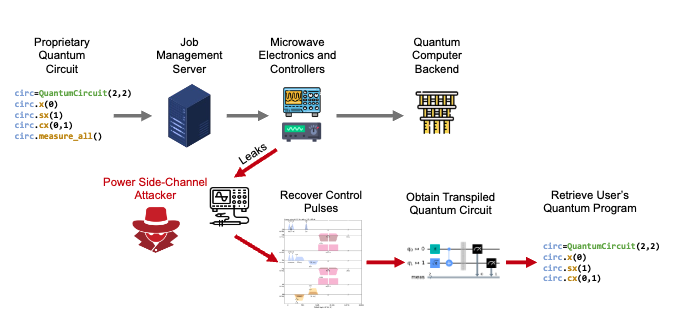
Quantum computing has seen a surge in interest in recent years, and with this increased attention comes the need for enhanced security measures for quantum circuits. A new type of threat has emerged, known as power trace attacks, which could potentially be launched by dedicated attackers. This threat involves the use of power traces to unlock and steal quantum circuit secrets.
Power traces can provide attackers with information about the control pulses sent to quantum computers. From these control pulses, the gate level description of the circuits and eventually the secret algorithms can be reverse engineered. This paper presents the first formalization and demonstration of using power traces for this purpose.
Two new types of single trace attacks have been identified: per-channel and total power attacks. The former relies on per-channel measurements to perform a brute-force attack to reconstruct the quantum circuits. The latter performs a single-trace attack using Mixed-Integer Linear Programming optimization.
How Effective are Power Trace Attacks on Quantum Circuits?
The use of algebraic reconstruction from power traces has shown that quantum circuit secrets can be stolen with high accuracy. An evaluation on 32 real benchmark quantum circuits showed that this technique is highly effective at reconstructing quantum circuits.
This research not only demonstrates the potential for these types of attacks but also highlights the need to develop new means to protect quantum circuits from power trace attacks. The study used real control pulse information from real quantum computers to demonstrate potential attacks based on the simulation of the collection of power traces.
The findings underscore the importance of securing quantum circuits, particularly as quantum computing becomes more accessible and widespread. With many quantum computers now available over the internet to researchers and everyday users, the threat of power trace attacks is more pertinent than ever.
What is the Role of Cloud-Based Quantum Computing Systems?
Due to the expensive nature of quantum computing equipment, these computers are often available as cloud-based systems. Companies such as IBM Quantum, Amazon Braket, and Microsoft Azure already provide access to various types of Noisy Intermediate-Scale Quantum (NISQ) devices from different vendors.
Remote access makes it easy for different users and companies to run algorithms on real quantum computers without the need to purchase or maintain them. However, this also means that users have no control over the physical space where the quantum computers are located.
While the cloud providers themselves may not be malicious, the threat of malicious insiders within data centers or cloud computing facilities is a well-known issue in classical security. These insiders may have physical access to the equipment of quantum computers and could potentially leverage this access to steal or leak quantum circuit secrets.
How Do Power Trace Attacks Compare to Other Side-Channel Attacks?
For classical computers, side-channel attacks of different types are a well-known threat. Two widely studied and analyzed side-channels are timing and power-based channels. In timing side-channel attacks, the attacker tries to learn some secret properties about the circuit by measuring the execution times.
Power side-channel attacks are more complex, where the attacker tries to establish a correlation between the power consumption and the operations and data that the circuit executes. These attacks require physical access to monitor the execution of the target computer.
Power side channels are well studied for classical computers, but understanding power side channels for quantum computers is a relatively new field of research. This work aims to address this gap and show how a malicious attacker can reconstruct a secret quantum circuit that is being executed by simply measuring the power consumption.
What are the Implications of Power Trace Attacks on Quantum Computers?
There is very limited research on understanding power side-channel attacks on quantum computers. One insight about quantum computers is that if the attacker is to perform physical measurements on the qubits during the computation, these measurements would interact with the qubits and destroy their state.
However, each quantum computer is controlled by external hardware such as microwave electronics and controllers. Quantum computers such as superconducting qubit machines from IBM, Rigetti, or others use microwave pulses to execute gate operations on qubits. The control pulses are fully classical and could be spied on, which is the target of this work.
This paper shows how by measuring the power consumption of the control hardware, an attacker could potentially reconstruct the quantum circuit that is being executed. This highlights the need for further research and development of security measures to protect quantum circuits from power trace attacks.
Publication details: “Quantum Circuit Reconstruction from Power Side-Channel Attacks on Quantum Computer Controllers”
Publication Date: 2024-03-12
Authors: Ferhat Erata, Changqing Xu, Ružica Piskač, Jakub Szefer, et al.
Source: IACR transactions on cryptographic hardware and embedded systems
DOI: https://doi.org/10.46586/tches.v2024.i2.735-768