Quantum key distribution offers a fundamentally secure method for generating encryption keys, but its practical implementation remains vulnerable to sophisticated eavesdropping attacks. Yuval Idan and Eliahu Cohen from Bar-Ilan University, alongside Tal Gofman, Ziv Abelson, Isabelle Cestier and Elad Mentovich from NVIDIA, investigate the effectiveness of two distinct eavesdropping strategies, one relying on subtle ‘probe-based’ measurements and the other employing a ‘probeless’ approach. Their research clarifies the theoretical differences between these methods and, crucially, demonstrates that the probeless technique can achieve significant information gain in a realistic, fibre-optic system compatible with data centre infrastructure. By experimentally validating a simplified quantum key distribution protocol, the team confirms the accuracy of their model and highlights the potential for practical, undetectable eavesdropping attacks that bypass traditional security measures. This work advances understanding of quantum hacking vulnerabilities and informs the development of more robust cryptographic systems.
Quantum key distribution (QKD) represents a provably secure method for generating a secret key, subsequently used for encoding and decoding information. This work analyses the effects of an eavesdropper’s variable-strength measurements on QKD systems. Two distinct measurement types are considered: a probe-based model, commonly referred to as a “weak measurement”, in which each qubit is weakly coupled to a continuous variable probe which is later projectively measured, and a probeless model, usually referred to as a “partial measurement”, where only a small, tunable fraction of all transmitted photons undergoes projective measurement, while the remainder are transmitted without disturbance. The investigation explores how these different eavesdropping strategies impact the security and performance of QKD protocols.
Quantum Key Distribution, Attack Mitigation and Tests
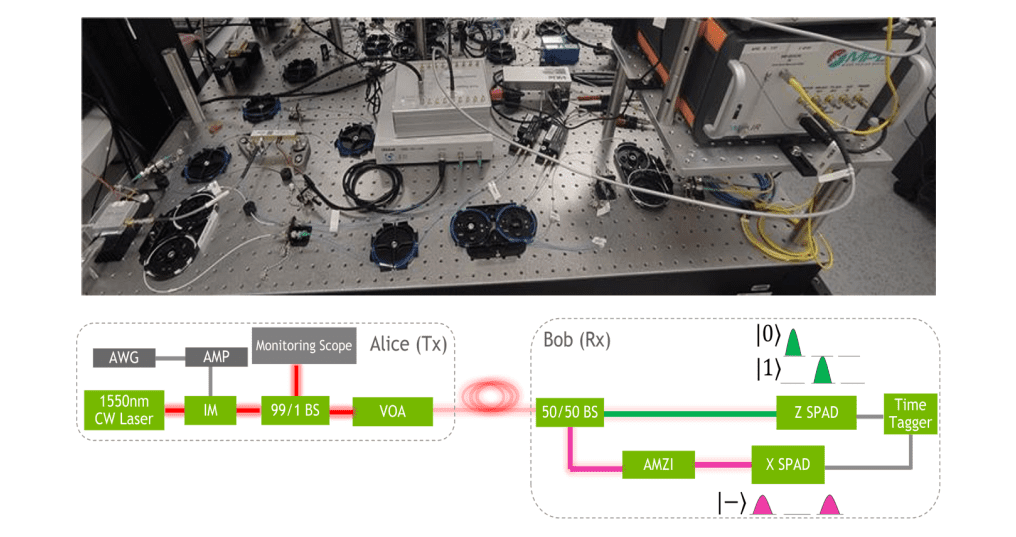
This research details a project focused on quantum key distribution (QKD), a simplified version of the BB84 protocol, and addresses potential vulnerabilities to improve performance. Scientists explored the use of weak and partial measurements to enhance security, and developed countermeasures against attacks such as photon number splitting and bright illumination. The goal is to provide a practical implementation of QKD, suitable for real-world applications, utilizing a 1550nm continuous wave laser, an intensity modulator, and fiber optics for signal transmission. Quantum key distribution relies on the principles of quantum mechanics to generate and distribute a secret key between two parties.
The BB84 protocol uses the polarization states of photons to encode information. Photon number splitting (PNS) attacks involve an eavesdropper intercepting photons, while bright illumination attacks overwhelm the quantum channel with light. Weak measurements extract limited information, minimizing disturbance, and partial measurements observe only a portion of the system. Decoy state protocols detect eavesdropping, and Mach-Zehnder interferometers manipulate the phase of light, crucial for QKD implementation. Single-photon avalanche diodes detect individual photons, and a time tagger precisely measures their arrival time.
The experimental setup includes an intensity modulator to create optical pulses, and implements eavesdropping and measurements using beam splitters and a Mach-Zehnder interferometer. Scientists employed decoy states to mitigate photon number splitting attacks and designed the system to be robust against bright illumination. This research aims to improve the security and performance of QKD systems and develop countermeasures against various attacks.
Eavesdropping Impacts on Quantum Key Distribution
Scientists have demonstrated a provably secure method for generating cryptographic keys, known as quantum key distribution (QKD), and analyzed the impact of an eavesdropper’s measurements on its security. The work focuses on two distinct eavesdropping approaches: one utilizing a probe to weakly interact with qubits, and another employing a “probeless” partial measurement of transmitted photons. Experiments were conducted using a time-bin-encoded Bennett-Brassard 1984 (BB84) protocol, designed for compatibility with data center environments. The team meticulously measured the information gained by the eavesdropper and the resulting quantum-bit-error-rate (QBER) for both measurement types.
Results demonstrate that the measured information gain and QBER closely match theoretical predictions across the full range of measurement strengths, validating the partial-measurement model and clarifying its relationship to established monitoring channels. This confirms the accuracy of the theoretical framework used to assess QKD security. Further analysis explored attacks combining photon number splitting and noise injection during calibration, revealing subtle differences between weak and partial measurements. The team’s measurements confirm that the eavesdropper’s information gain can theoretically reach 100% when measurements are performed in the time basis. This research delivers a comprehensive understanding of eavesdropping strategies in QKD systems and provides crucial validation for the security of practical implementations, particularly within data center networks.
Eavesdropping Attacks Expose QKD Vulnerabilities
This research presents a detailed analysis of eavesdropping attacks on quantum key distribution (QKD) systems, specifically examining the impact of variable-strength measurements. The team investigated two distinct approaches: probe-based “weak” measurements and “probeless” partial measurements. Through theoretical modelling and experimental validation, they demonstrated that both methods allow an eavesdropper to gain information about the secret key, but with differing levels of effectiveness. Importantly, the researchers successfully implemented a practical eavesdropping attack on a simplified QKD protocol within a data-center environment, confirming the feasibility of these attacks in real-world systems.
Furthermore, the team explored the impact of combining photon number splitting with weak measurements, and demonstrated a noise-injection attack targeting the calibration of QKD systems. The experimental results closely matched theoretical predictions across a range of measurement strengths, validating the partial-measurement model and providing a deeper understanding of eavesdropping strategies. This research contributes to a more comprehensive understanding of QKD security and informs the development of more robust quantum communication systems.
👉 More information
🗞 Probeless vs Probe-Based Variable-Strength Eavesdropping in Quantum Key Distribution
🧠 ArXiv: https://arxiv.org/abs/2509.25890