Maintaining trust in digital information requires robust methods to verify authorship and prevent tampering, a challenge increasingly critical for blockchain technologies. Kaveri Banerjee and Sajal Saha, both from Adamas University, comprehensively investigate digital signature schemes used within blockchain systems, revealing how these schemes underpin the security and reliability of decentralised ledgers. Their work assesses various signature designs against key criteria such as unforgeability and scalability, demonstrating how different approaches impact system performance and resilience to attack. This research underscores the vital role of carefully selected digital signatures in guaranteeing non-repudiation and preserving data integrity, offering valuable insights for the ongoing development and implementation of secure blockchain technologies.
Blockchain technology, with its inherent decentralised ledger and robust security, possesses significant potential and has gained considerable attention. Non-repudiation is a critical component of information security within these blockchain systems, and can be effectively ensured through the implementation of digital signature schemes. This study analyses digital signatures as they are used in blockchain technology, focusing specifically on their role in achieving non-repudiation and preserving information integrity.
Blockchain and Cryptocurrency Applications Overview
Researchers have extensively investigated blockchain technology and its applications across various domains, providing comprehensive overviews of the technology and its implications. Investigations also cover the application of blockchain in diverse fields, including the Internet of Things, and detailed analyses of its security and privacy considerations.
Non-Repudiation and Digital Signature Scheme Analysis
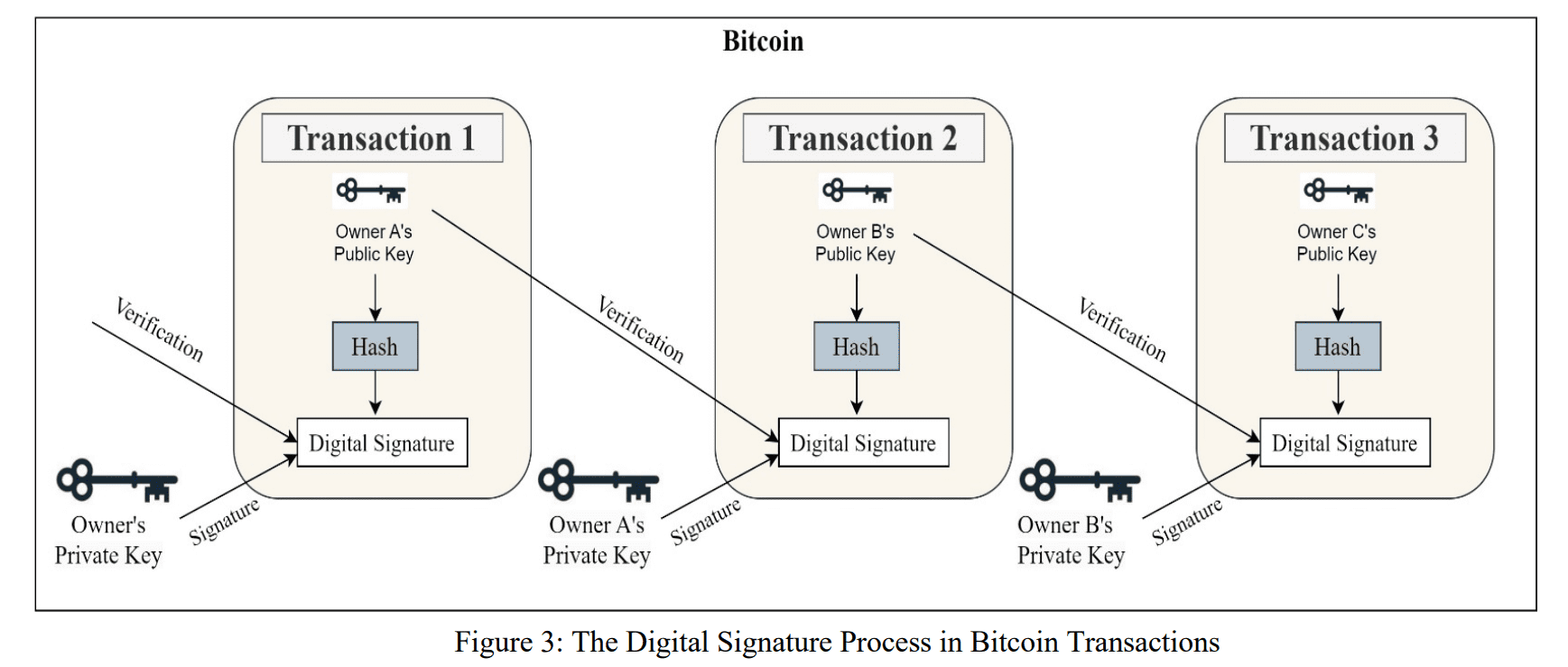
This work delivers a comprehensive analysis of digital signature schemes crucial for blockchain technology, focusing on their ability to guarantee non-repudiation and maintain data integrity. Researchers established key criteria for evaluating these schemes, including the capacity to provide irrefutable evidence of signing, data integrity detection, and underlying cryptographic properties such as unforgeability. The study meticulously analysed security assumptions and performance metrics, assessing computational efficiency, signature sizes, and verification times to determine suitability for diverse blockchain applications. Investigations revealed that achieving non-repudiation relies on employing digital signatures based on asymmetric encryption, often utilising elliptic curve equations, as demonstrated within the Bitcoin framework.
The process confirms that possession of a private key allows a sender to cryptographically prove ownership and authorize transactions, providing a verifiable record that cannot be disputed. Researchers confirmed that any network participant can validate this ownership and the transaction’s legitimacy. The methodology involved a detailed comparison of various signature schemes, including aggregate, group, ring, blind, and proxy signatures, when applied to blockchain systems. This evaluation identified algorithms capable of effectively addressing unique security, performance, and scalability requirements across different applications, from cryptocurrency transactions to smart contracts and the Internet of Things.
Blockchain Signatures, Efficiency and Scalability Tradeoffs
This research presents a comprehensive analysis of digital signature schemes as they apply to blockchain technology, demonstrating their critical role in ensuring non-repudiation and data integrity. The study systematically compares several prominent schemes, including RSA, DSA, and ECDSA, evaluating their performance characteristics in the context of blockchain constraints and requirements. Results indicate that ECDSA currently offers the most favourable balance of security, efficiency, and scalability for blockchain applications, although conventional methods face limitations as demands on blockchain systems increase. The work highlights the importance of careful selection of digital signature schemes to address practical tradeoffs affecting throughput, storage, and security, and it proposes avenues for future development.
Researchers acknowledge the need for ongoing investigation into lattice-based and aggregate signature techniques to improve scalability, enhance privacy, and overcome the limitations of existing methods. Future work will focus on these advanced techniques, particularly in the context of integrating blockchain with resource-constrained devices such as those found in the Internet of Things, and exploring methods to improve transaction anonymity through techniques like ring and blind signatures. These developments aim to establish stronger, more efficient, and scalable digital signature implementations, ultimately bolstering the trustworthiness of blockchain systems.
👉 More information
🗞 Blockchain Signatures to Ensure Information Integrity and Non-Repudiation in the Digital Era: A comprehensive study
🧠 ArXiv: https://arxiv.org/abs/2510.22561