Quantum key distribution promises secure communication, and the decoy-state BB84 protocol currently forms the basis for many practical systems. Akihiro Mizutani from the University of Toyama, Shun Kawakami from NTT Inc., and Go Kato now provide a crucial theoretical advance by rigorously proving the security of this protocol when the receiver makes measurements passively. This passive approach simplifies the system, reducing the need for complex and potentially vulnerable components, yet a complete security analysis had remained elusive until now. The team’s work delivers a clear formula for calculating the secure key generation rate, demonstrating that passive measurement performs almost identically to more complex active methods, and paving the way for simpler, more efficient quantum communication networks.
This work addresses the challenges posed by imperfect detection and potential side-channel attacks, establishing tighter security bounds than previously known. Researchers developed a comprehensive framework that accounts for real-world imperfections, including detector efficiencies, background noise, and the statistical fluctuations inherent in limited data sets. The method carefully estimates the information leaked to an eavesdropper, Eve, during quantum transmission and subsequent classical communication.
By accurately modelling these imperfections, the team derives a secure key rate, representing the maximum length of a secret key that can be reliably extracted from the raw data. This analysis specifically considers the characteristics of passive measurement, where the receiver’s detector choice is independent of the incoming quantum signal. The team’s contributions include a refined estimation of the error correction parameters needed to eliminate errors introduced by channel noise and eavesdropping, demonstrating that optimising these parameters significantly improves key generation efficiency and security. Furthermore, the analysis provides a detailed understanding of the trade-offs between key rate, transmission distance, and device imperfections. The results show that, even with realistic device parameters, the decoy-state BB84 QKD protocol with passive measurement can achieve secure communication over substantial distances. This work advances the practical implementation of QKD systems and contributes to the development of secure communication networks.
Decoy-State BB84 Protocol Security Analysis
Quantum key distribution (QKD) establishes secure communication by generating and distributing encryption keys using the principles of quantum mechanics. The goal is to create a secret key between two parties, Alice and Bob, in a way that any eavesdropping attempt by Eve will be detectable. Key concepts include the BB84 protocol, decoy-state QKD, and finite-key analysis, which addresses the limitations of real-world systems with limited data. Decoy-state QKD improves upon the basic BB84 protocol by addressing imperfections in single-photon sources. It involves sending decoy pulses alongside signal pulses to estimate channel characteristics and detect eavesdropping.
Finite-key analysis is crucial because it provides security bounds for practical systems with a limited number of key exchanges. Researchers also employ techniques like composable security, twin-field QKD, and various encoding methods to enhance QKD performance and security. A significant portion of research focuses on the mathematical and statistical techniques used to prove the security of QKD systems. This includes concentration inequalities, Renyi entropy, adversarial setups, error correction, and privacy amplification. These tools are essential for rigorously analysing the security of QKD protocols and ensuring their resilience against attacks. Real-world QKD systems are not perfect, and researchers address practical considerations such as detection efficiency mismatch, channel imperfections, single-photon source imperfections, detector imperfections, and Trojan-horse attacks. By addressing these challenges, scientists strive to develop robust and reliable QKD systems that can withstand real-world conditions.
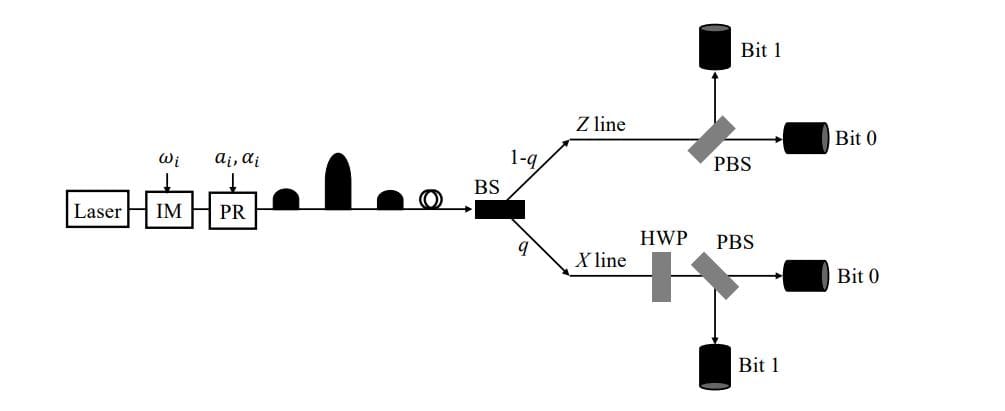
Decoy-State BB84 Security with Passive Bases
Scientists have successfully demonstrated the security of a practical quantum key distribution (QKD) protocol, specifically the decoy-state BB84 protocol, when the receiver employs a passive basis choice. This achievement provides a fully analytical proof for this implementation, yielding a formula to directly calculate the secret-key rate using parameters readily obtained from experiments. The research simplifies the security analysis by eliminating the need to estimate the receiver’s single-photon detection rate. The team demonstrated that the passive measurement approach achieves a key generation rate comparable to traditional active measurement implementations, indicating no compromise in efficiency.
Numerical simulations reveal that performance is strongly linked to the quality of photon detectors; better detectors minimize the difference between active and passive setups, enabling long-distance QKD over distances exceeding 245 kilometers. The analysis successfully bounds discrepancies in error rates between the two approaches, attributing them to the typically negligible cross-click rate of detectors. While this work focused on passive measurement by the receiver, the scientists acknowledge the potential for extending the analysis to a fully passive BB84 protocol, encompassing passive state preparation by both parties. Future research will likely explore this direction to further simplify QKD systems and broaden their applicability.
👉 More information
🗞 Finite-key security analysis of the decoy-state BB84 QKD with passive measurement
🧠 ArXiv: https://arxiv.org/abs/2511.21253