The looming threat of quantum computers necessitates a shift towards new cryptographic methods, and a recent study assesses how well existing software tools are prepared for this change. Nadeem Ahmed, Lei Zhang, and Aryya Gangopadhyay, all from the University of Maryland Baltimore County, investigated the support for post-quantum cryptography (PQC) within nine popular open-source cryptographic libraries, including OpenSSL and Bouncy Castle. Their analysis reveals a mixed landscape of preparedness, with some libraries actively integrating PQC algorithms like CRYSTALS-Kyber and CRYSTALS-Dilithium, while others still lack substantial support. This research is significant because it identifies critical gaps in current cryptographic infrastructure, highlighting the urgent need for coordinated efforts to ensure a secure transition to a quantum-resistant future and mitigate potential security risks as quantum computing technology advances.
The study details key findings and takeaways regarding the preparedness of these libraries for a post-quantum future. The paper emphasizes the urgent need to transition to PQC due to the potential of quantum computers to compromise widely used public-key cryptosystems. Governments and major technology companies are actively preparing for this transition, while standards bodies like NIST are finalizing PQC algorithms.
The research assesses PQC support in several key libraries, revealing a varied landscape of progress. wolfSSL/wolfCrypt emerges as a leading library with strong and early PQC support, including implementations of NIST-selected algorithms such as Kyber, Dilithium, Falcon, and SPHINCS+. OpenSSL, historically slower to adopt PQC, is now incorporating these algorithms, though integration remains ongoing. Bouncy Castle offers PQC implementations, particularly for Java and C#, and is actively updating to support the latest standards. Botan provides PQC support and is a versatile library used in various applications.
LibreSSL and mbed TLS also demonstrate increasing PQC support, though at a slower pace compared to wolfSSL. Integrating PQC algorithms into existing libraries presents challenges related to performance, code size, and compatibility with existing protocols. PQC algorithms generally exhibit different performance characteristics than classical algorithms, often requiring larger key sizes and more computational resources. NIST’s standardization process is crucial, and the selected algorithms, Kyber, Dilithium, Falcon, and SPHINCS+, are central to the transition. Combining classical and PQC algorithms in hybrid approaches is a common strategy to provide both security and compatibility during this period, particularly within the widely used TLS protocol.
PQC is particularly important for securing Internet of Things (IoT) devices, which often have limited resources and long lifecycles. Protecting critical infrastructure from quantum attacks is a high priority, and data requiring long-term confidentiality is vulnerable to future quantum attacks and requires PQC protection. Future work should focus on optimizing PQC algorithms, finalizing and widely adopting standards, leveraging hardware acceleration, and deploying PQC in real-world applications. This paper provides a valuable snapshot of the current state of PQC implementation, highlighting progress, challenges, and the importance of preparing for the quantum era.
Post-Quantum Crypto Library Implementation Survey
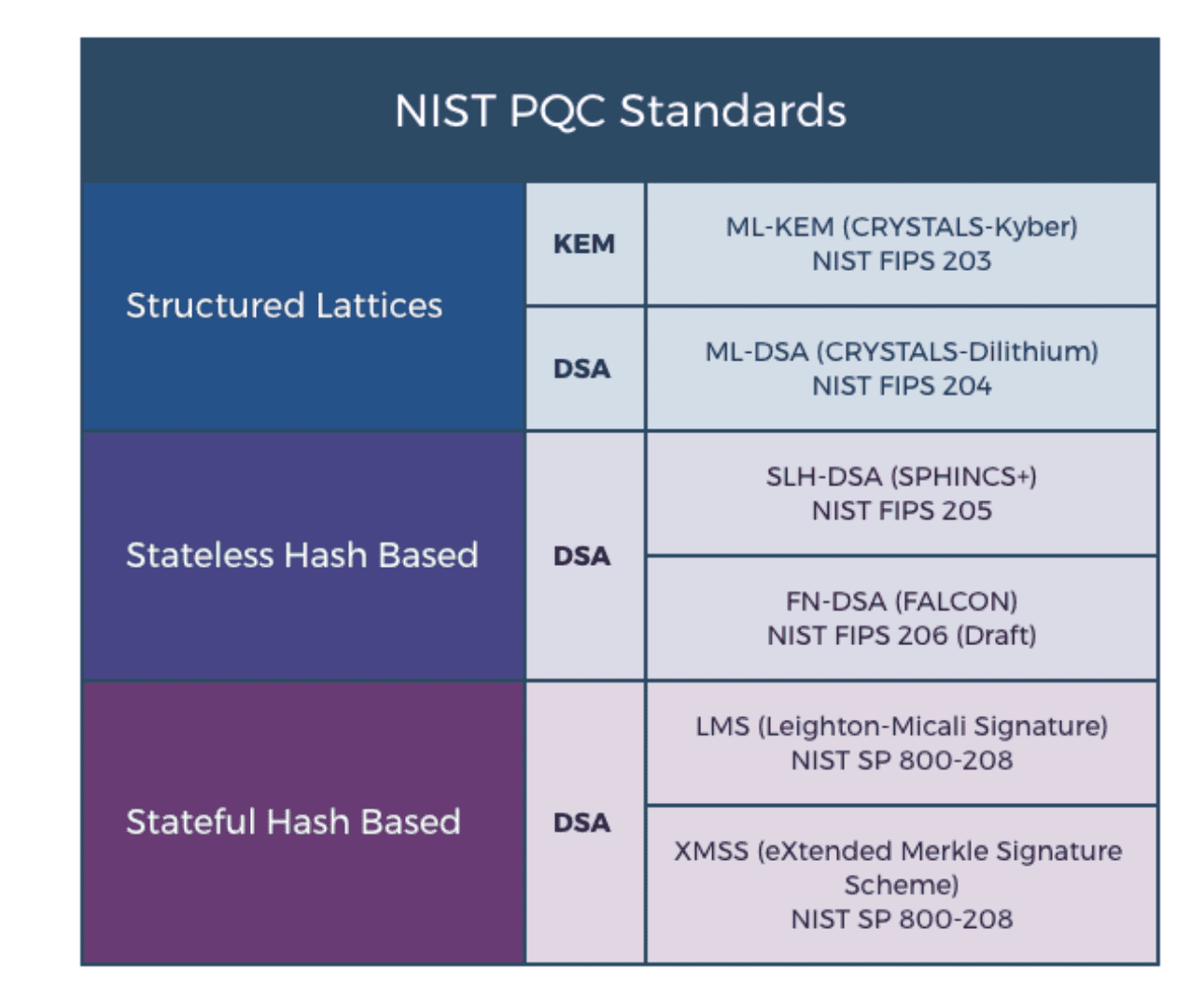
Researchers undertook a comprehensive survey of nine widely used open-source cryptographic libraries to assess their preparedness for post-quantum cryptography (PQC). The study focused specifically on implementation support for the algorithms selected by the National Institute of Standards and Technology (NIST) following its multi-year standardization process, initiated to address vulnerabilities posed by advancing quantum computing. The core of the research involved identifying the extent to which each library supported the four NIST-selected PQC algorithms: CRYSTALS-Kyber, a key encapsulation mechanism; CRYSTALS-Dilithium, a lattice-based digital signature scheme; FALCON, another lattice-based signature algorithm optimized for smaller signature sizes; and SPHINCS+, a stateless hash-based signature scheme offering a different security foundation. Researchers also noted support for older stateful hash-based signatures like Leighton-Micali and XMSS, to provide a broader picture of PQC implementation.
This detailed examination allowed scientists to map the current landscape of PQC support within these critical cryptographic tools. To ensure a rigorous and comparable assessment, the team established clear criteria for defining a “supported” algorithm, focusing on practical implementation within the libraries rather than theoretical compatibility. By maintaining a high-level conceptual focus, the team aimed to provide actionable insights for decision-makers and developers navigating the evolving cryptographic landscape. The research methodology mirrored the rigor of the NIST standardization process itself, acknowledging the importance of both security and performance. Scientists considered factors such as key and ciphertext sizes, computational efficiency on diverse platforms, and potential patent implications when evaluating each library’s implementation. This holistic approach allowed for a nuanced understanding of the trade-offs involved in adopting PQC algorithms and informed a comprehensive assessment of the current state of PQC readiness within the open-source cryptographic community.
Post-Quantum Crypto Support in Open-Source Libraries
This research comprehensively evaluates the support for post-quantum cryptographic (PQC) algorithms within nine widely used open-source cryptographic libraries. The analysis reveals a varied landscape of preparedness, with some libraries actively integrating PQC algorithms and others lagging behind, despite the growing threat to current cryptographic systems posed by advances in computing. Researchers examined support for CRYSTALS-Kyber, a key encapsulation mechanism, and three digital signature schemes, recognizing the importance of both encryption and authentication in a post-quantum world. The study also considered support for older, stateful hash-based signature schemes like the Leighton-Micali Signature and the eXtended Merkle Signature Scheme, acknowledging their role as potential interim solutions. By surveying these widely adopted libraries, the research provides a clear picture of the current state of PQC implementation and highlights the challenges and opportunities for ensuring a secure transition to quantum-resistant cryptography. The findings underscore the urgent need for continued research, standardization efforts, and coordinated adoption strategies to protect sensitive data in the face of evolving quantum threats.
👉 More information
🗞 A Survey of Post-Quantum Cryptography Support in Cryptographic Libraries
🧠 ArXiv: https://arxiv.org/abs/2508.16078