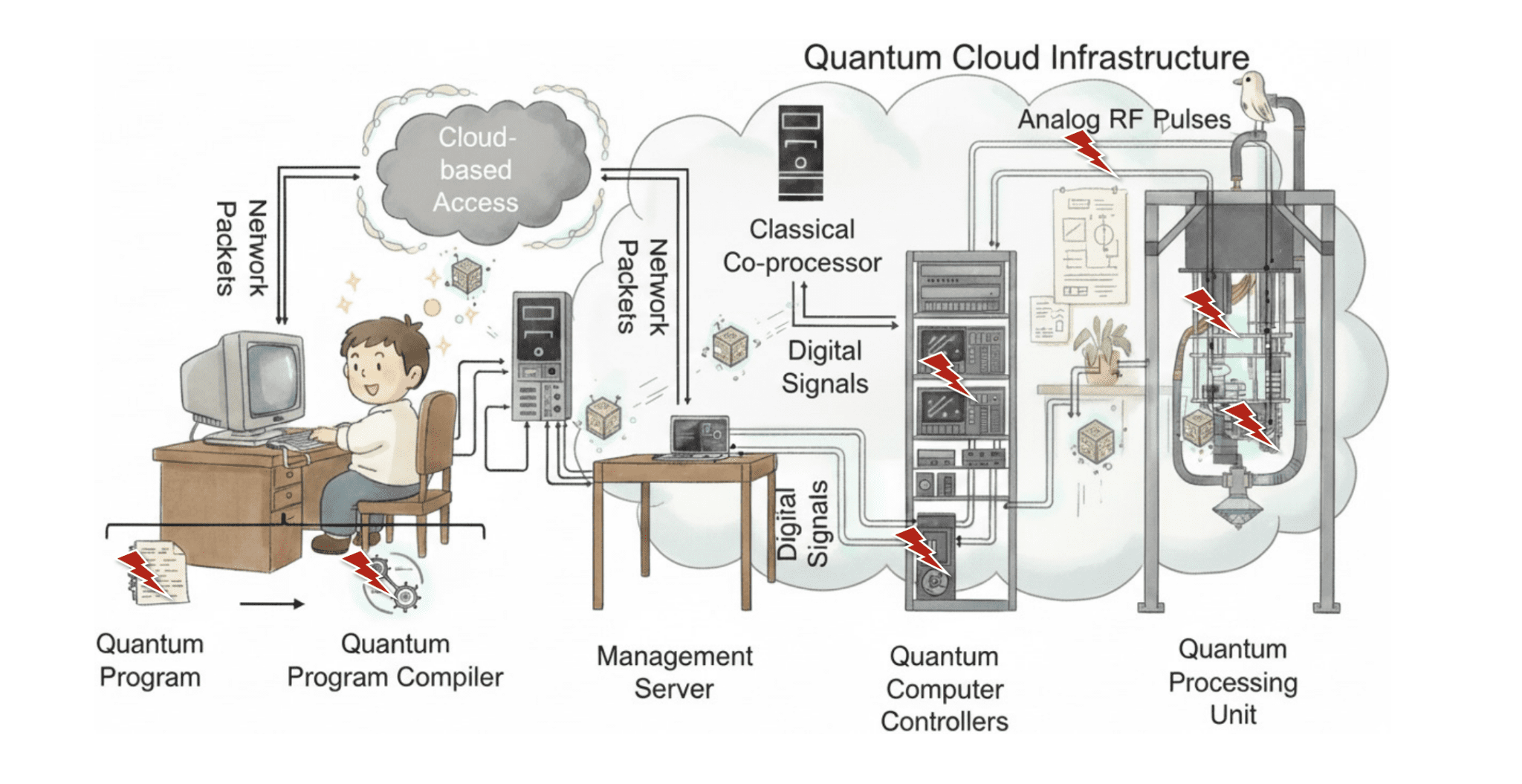
Quantum computing represents a rapidly advancing technological frontier, poised to solve problems beyond the reach of conventional supercomputers. Sanjay Deshpande and Jakub Szefer, both from Northwestern University, investigate a critical, yet often overlooked, aspect of this emerging field: its inherent security vulnerabilities. While much attention focuses on developing cryptographic methods to defend classical systems against quantum attacks, this work introduces the complementary challenge of protecting quantum computers themselves from malicious interference. By exploring the unique security landscape of quantum processors, the researchers highlight the need for proactive measures to safeguard these powerful machines and ensure the integrity of future quantum computations.
Quantum computing is rapidly emerging as one of the most transformative technologies of our time. With the potential to tackle problems intractable for even the most powerful classical supercomputers, quantum hardware has advanced at an extraordinary pace, with major platforms such as IBM Quantum, Amazon Braket, and Microsoft Azure providing cloud-based access. While promising, quantum computing is not immune to security threats, prompting extensive research into post-quantum cryptography and, increasingly, the security of quantum computers themselves. One security advantage of quantum systems lies in the no-cloning theorem.
Qubit Crosstalk Mitigation and Side-Channel Defenses
Researchers are actively developing methods to secure quantum computers against potential attacks, recognizing vulnerabilities specific to the quantum realm. A key focus involves mitigating crosstalk, the unwanted interaction between qubits, which can leak information. Scientists employ precise measurement techniques to characterize and minimize these interactions between transmon qubits, analyzing magnetic flux to understand signal interference. To defend against side-channel attacks, researchers are pioneering techniques to obscure internal operations and prevent attackers from inferring sensitive data from physical characteristics.
One approach involves developing quantum Physical Unforgeable Functions (PUFs), leveraging inherent variations in qubit behavior to create unique, device-specific fingerprints based on single-qubit gates. This provides a hardware-based security layer, authenticating devices and protecting against cloning. Further work explores split compilation, dividing quantum circuits into multiple parts to enhance security by making reverse engineering more difficult. Scientists are also designing trusted execution environments for quantum computers, creating isolated regions where computations can occur without interference. Dynamic pulse switching offers a means of protecting computations running on untrusted cloud platforms, and researchers investigate securing reset operations against attacks that attempt to manipulate qubits.
Qubit Crosstalk Reveals Quantum Side-Channel Threats
Recent work demonstrates that quantum computing is vulnerable to a range of security threats demanding proactive countermeasures. Researchers have meticulously characterized qubit coupling mechanisms, revealing how malicious circuits can degrade computation fidelity sharing the same quantum processor. Experiments show that crosstalk induces side-channel threats, leaking sensitive information through timing analysis of reset operations and power consumption traces. Standard reset gates were found to improperly clear qubit states, allowing information to leak between consecutively executed circuits, a fundamental flaw in system isolation.
The security of quantum compilers has also emerged as a critical concern, as malicious or compromised compilers can directly threaten intellectual property through circuit theft. Sophisticated attacks, such as the QTrojan, demonstrate the ability to stealthily disable data encoding by manipulating hardware configuration files disguised as routine pulse calibrations. To counter these threats, the research community is developing defenses across multiple layers, including Quantum Trusted Execution Environments, Quantum Physical Unclonable Functions (QPUFs), and device fingerprinting. Circuit watermarking and obfuscation techniques preserve functionality while obscuring implementation details, protecting intellectual property in cloud deployments, and quantum antivirus systems utilize subgraph isomorphism detection to identify malicious circuit patterns that induce crosstalk.
Circuit splitting approaches distribute computations across multiple quantum processors, limiting information exposure to any single provider. Researchers have categorized quantum security threats into three classes: information leak attacks, untargeted attacks degrading system performance, and targeted attacks leveraging deep system knowledge. Measurements confirm that these attacks exploit vulnerabilities to extract sensitive data, opportunistically degrade performance, or achieve precise malicious goals, establishing a foundation for building trustworthy, resilient quantum systems.
Quantum Security Risks and Mitigation Strategies
Researchers are increasingly focused on the security of quantum computers, recognizing that these powerful machines are not inherently immune to attack. This work demonstrates that, similar to classical computers, quantum systems are vulnerable to a range of security threats, including side-channel attacks, reset operation attacks, and potential backdoors within quantum neural networks. Investigations have revealed vulnerabilities in both the quantum processing units and the classical control systems responsible for operating them, highlighting the need for comprehensive security measures. The team explored several approaches to mitigate these risks, including techniques for circuit obfuscation, watermarking, and the development of trusted execution environments tailored for quantum hardware. Furthermore, researchers are investigating methods to protect against power side-channel attacks by dynamically switching pulses and securing reset operations against manipulation. While significant progress has been made in identifying vulnerabilities and proposing countermeasures, current solutions are not exhaustive and require further refinement, with future work likely focusing on developing more robust security protocols, improving the resilience of quantum hardware, and exploring novel cryptographic techniques specifically designed for the quantum realm.
👉 More information
🗞 What is Quantum Computer Security?
🧠 ArXiv: https://arxiv.org/abs/2510.07334