Quantum Key Distribution (QKD) offers an unparalleled level of security for exchanging cryptographic keys, relying on the laws of physics rather than computational complexity to protect information, and becoming increasingly vital as conventional encryption methods face growing threats. However, practical QKD systems are vulnerable to various attacks, including Trojan-Horse attacks where an eavesdropper injects light to analyse reflected signals, and researchers are actively working to address these weaknesses. Alberto De Toni, Aynur Cemre Aka, Costantino Agnesi, and colleagues, at institutions including the University of Padova, investigate vulnerabilities in a specific QKD encoder, the iPOGNAC, and propose countermeasures to mitigate these Trojan-Horse attacks. This work represents a significant step towards securing QKD systems and enabling the development of a truly secure global communication network, by proactively addressing potential weaknesses in critical components.
Unlike classical cryptographic systems, the security of QKD is not reliant on computational assumptions but is instead rooted in the fundamental laws of physics. In a QKD protocol, any attempt by an eavesdropper to intercept the key is detectable, providing an unprecedented level of security and making QKD an attractive solution for secure communication. The study identifies that QKD systems are susceptible to attacks where an eavesdropper manipulates the quantum signals exchanged between legitimate parties by injecting extra photons or altering signal characteristics to gain information about the key. Real-world detectors possess limitations like dead time, saturation, and varying detection efficiencies, which attackers can exploit, deviating from the ideal conditions often assumed in theoretical security proofs. The research explores various aspects of QKD security, including analyzing how Trojan-horse attacks can bypass existing security protocols.
Detailed characterization of detector performance, including dead time, saturation, and efficiency, reveals how these limitations can be exploited. The team developed and evaluated methods to counter Trojan-horse attacks and improve the security of QKD systems, including monitoring the characteristics of the quantum source to detect anomalies indicative of an attack. Detector calibration and compensation reduce vulnerabilities, while advanced data post-processing techniques filter out malicious signals and improve key generation rates. The team also developed new QKD protocols that are more robust to attacks and detector imperfections.
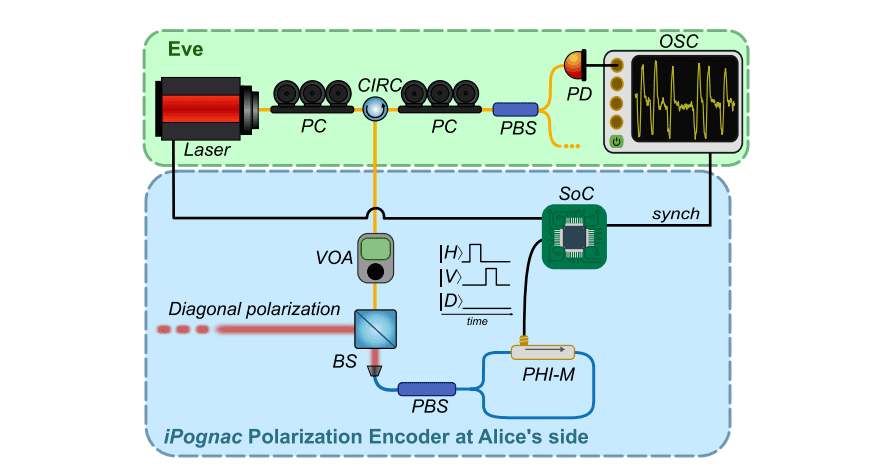
The research considers the entire QKD system, including the source, channel, and detectors, to identify and address potential vulnerabilities. Analysis of different types of optical fibers reveals their impact on QKD performance and security, while assessment of the damage thresholds of optical fibers to high-power laser attacks further enhances system resilience. Improvements to synchronization methods enhance QKD performance and security. Researchers investigated the iPOGNAC encoder, a device used to generate quantum states for secure communication, and developed countermeasures to mitigate these attacks. They successfully demonstrated the ability to maintain low quantum bit error rates (QBER) over extended periods, both in laboratory settings and during field trials, highlighting the device’s versatility for robust quantum networks. Experiments focused on a Trojan-Horse attack setup where an eavesdropper injects light into the system and analyzes the reflected signal, allowing for precise quantification of the countermeasures’ effectiveness.
The team explored the theoretical limits of information extraction by an eavesdropper, revealing that the accessible information is bounded by the Holevo bound, a key concept in quantum information theory, and limited by the Von Neumann entropy of the quantum state. Further analysis focused on practical detection schemes, calculating guessing probabilities for different detector types, including photon-number resolving detectors and Geiger-mode detectors, demonstrating the trade-offs between detector performance and the security of the QKD system. The team investigated how an eavesdropper might inject light into the system to gain information about the key, and subsequently developed and evaluated countermeasures to mitigate these attacks. Their findings demonstrate that Trojan-Horse attacks pose a genuine threat to the security of QKD systems, but can be effectively addressed through careful design and implementation of appropriate safeguards, with a combination of countermeasures offering the most robust defense. Specifically, the researchers determined that achieving an attenuation of approximately 65-70 decibels at the output of the iPOGNAC is sufficient to ensure security against the examined attack vectors, limiting the information available to an eavesdropper.
Current QKD systems already employ around 50 decibels of attenuation, suggesting that a relatively modest increase in this parameter, alongside the addition of an isolator, can significantly enhance security. The authors acknowledge that their analysis is based on specific assumptions regarding the attacker’s capabilities and the system’s parameters, and that future work could explore the effectiveness of these countermeasures against more sophisticated attack strategies or investigate the impact of imperfections in real-world components. Nevertheless, this research provides valuable insights into the practical security of QKD systems and offers concrete guidance for improving their resilience against a significant class of threats.
👉 More information
🗞 Countermeasures for Trojan-Horse Attacks on self-compensating all-fiber polarization modulator
🧠 ArXiv: https://arxiv.org/abs/2510.16868