Quantum key distribution offers the promise of perfectly secure communication, but defining and measuring that security presents a significant challenge. Carla Ferradini, Martin Sandfuchs, and Ramona Wolf, alongside Renato Renner from ETH Zurich and the Universität Siegen, now provide a rigorous definition of a key parameter, denoted as, that quantifies the security of quantum key distribution. This work establishes that, under realistic physical conditions, represents a concrete, explicit bound on the probability of communication failure, unlike traditional cryptographic methods which rely on assumptions about computational difficulty. By adopting a clear axiomatic approach, the researchers demonstrate a fundamental understanding of this security measure and directly address existing criticisms, ultimately strengthening the foundations of secure quantum communication.
Distinguishability Proofs for Quantum Key Distribution Security
This appendix provides the mathematical proofs and lemmas that underpin the security claims made in a related paper on quantum key distribution (QKD). It rigorously establishes the properties of a specific measure of distinguishability between quantum states, known as the maximum distinctness probability, and how this relates to the security of QKD protocols. The work delves into the mathematical foundations of secure communication using quantum mechanics. Key concepts include quantum key distribution, which uses quantum mechanics to securely distribute cryptographic keys; density operators, mathematical representations of quantum states; and trace distance, a measure of how distinguishable two quantum states are, with larger distances indicating easier differentiation.
The maximum distinctness probability is a specific measure used in this work to quantify the information an eavesdropper might gain about the key. The appendix begins by defining the mathematical objects and notation used throughout the proofs. One key lemma establishes a lower bound on the modified maximum distinctness probability, demonstrating it is at least half the trace distance between two states, connecting it to a standard measure of distinguishability. Another lemma proves that applying a quantum channel or an eavesdropper’s action cannot decrease the distinguishability of states, a crucial principle in QKD security analysis.
Further lemmas establish properties of the maximum distinctness probability, including that it is zero only when the states are identical, and that applying a quantum channel cannot decrease it. A final lemma provides a mathematical expression for the probability that Alice and Bob end up with different keys after the QKD protocol, relating this to the difference between the actual key state and a hypothetical state. This result is crucial for proving the correctness of the QKD protocol, demonstrating that the probability of key mismatch can be controlled and minimized. In essence, this appendix provides the rigorous mathematical foundation for the security analysis of a QKD protocol, establishing the properties of a specific measure of distinguishability and its relation to key correctness and security.
QKD Security, Error Probability, and Axiomatic Foundations
The security of quantum key distribution (QKD) relies on a parameter that, under defined physical assumptions, can be explicitly bounded, unlike computationally-based schemes where security claims are typically asymptotic. This work adopts an axiomatic approach to demonstrate that this parameter represents the maximum probability of a failure occurring within the key distribution process, providing a concrete interpretation of its significance. Researchers rigorously examined the foundations of this parameter to establish its role in quantifying the inherent limitations of QKD systems. Scientists investigated the theoretical underpinnings of QKD security by establishing a direct link between the parameter and the probability of error in the key exchange.
The study involved a detailed analysis of the axiomatic framework, allowing researchers to define the parameter as the highest possible chance of a system failing to generate a secure key. This approach contrasts with traditional methods that rely on approximations or assumptions about the underlying physical processes. The team meticulously constructed a mathematical model to demonstrate this relationship, ensuring the clarity and precision of the definition. Furthermore, the research addressed criticisms of this definition, responding to concerns raised in existing literature. The team systematically reviewed these critiques, providing detailed rebuttals and clarifying potential misunderstandings.
This involved a careful examination of the assumptions underlying the definition and a demonstration of its consistency with established principles of quantum mechanics and information theory. This study pioneers a robust and defensible framework for understanding the security of QKD, strengthening its foundation as a secure communication technology. Scientists also explored the implications of this definition for the practical implementation of QKD systems. By explicitly bounding the probability of failure, the research provides a clear benchmark for evaluating the performance of real-world devices, allowing engineers to design and optimize QKD systems with greater confidence.
Formal QKD Security with Arbitrary Parameters
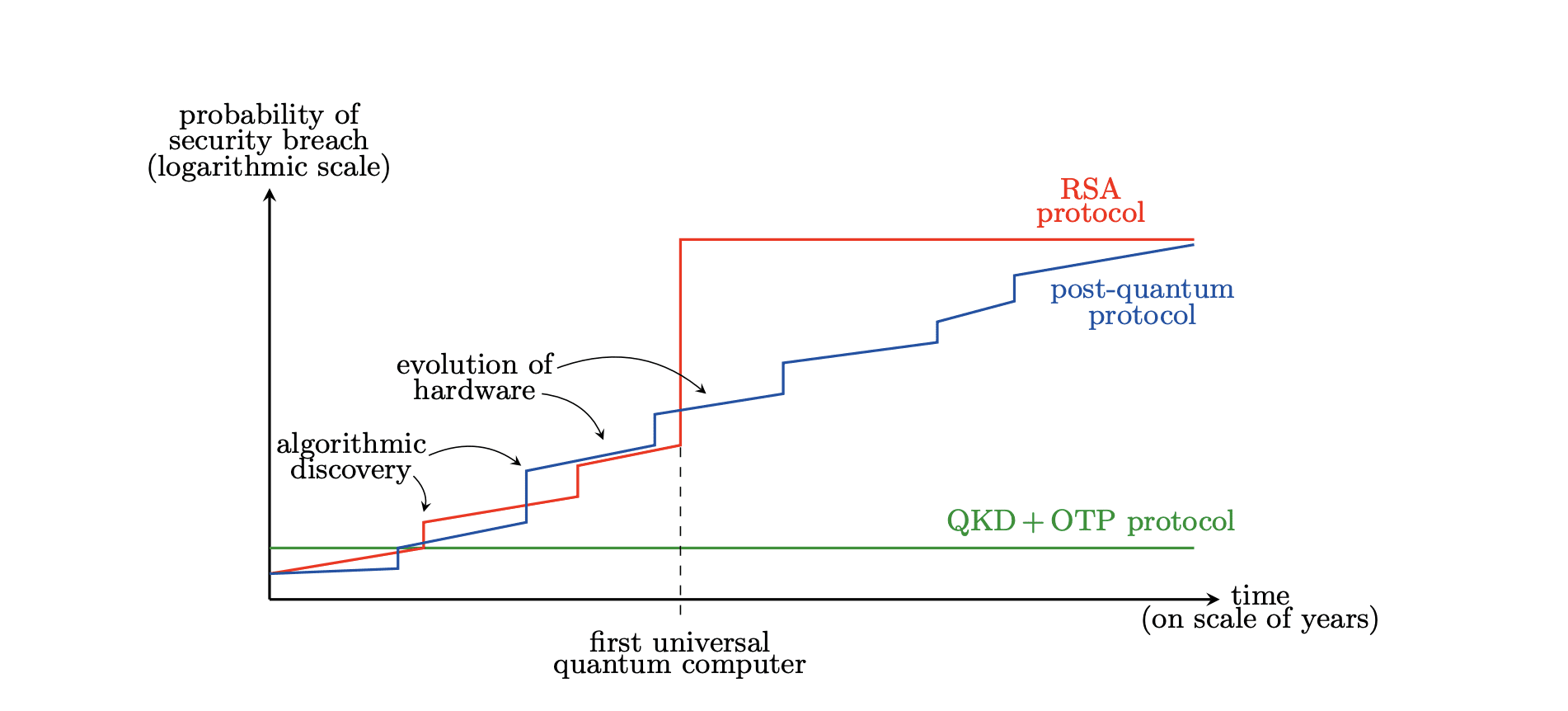
This work establishes a rigorous understanding of security parameters in quantum key distribution (QKD), defining ε as the maximum probability of a security failure. Researchers demonstrate that a QKD protocol achieves εQKD-security when no information about the key leaks to an adversary except with probability εQKD, regardless of the attack strategy employed. This framework leverages the union bound, enabling composability, meaning the overall security parameter of a system combining QKD with one-time pad (OTP) encryption is simply εtotal = εQKD, since OTP offers perfect secrecy. Experiments confirm that the security parameter ε can be made arbitrarily small, with typical QKD protocols requiring resources that scale only polylogarithmically with 1/εQKD.
The team formalised this operational meaning of ε, interpreting it as a probability to enable a clear understanding of security claims. Researchers established a framework to model the knowledge an adversary might acquire about the key, acknowledging underlying assumptions such as the correctness of quantum theory and the security of laboratory access. The study introduces notation for key concepts in quantum information theory, including Hilbert spaces, density operators, and reduced density operators, providing a foundation for detailed analysis. For instance, the reduced density operator ρA, obtained by tracing out system B from the joint density operator ρAB, describes the state of system A alone. Furthermore, the team defines classical-quantum states ρXA, describing correlations between a classical random variable X and a quantum system A, and the associated conditional state ρXA|Ω, which describes the state conditioned on an event Ω. These definitions provide a precise language for quantifying security and analysing the performance of QKD protocols.
Epsilon Security, Adversarial Models, and QKD Validity
This work clarifies the foundations of quantum key distribution (QKD) security by establishing a rigorous connection between theoretical models and practical implementation. Researchers demonstrate that the security of a QKD protocol can be quantified using a parameter, ε, which represents the maximum probability of key failure. This definition, now widely adopted within the field, allows for a meaningful assessment of security levels and a balance between security and practical design considerations. The team addressed criticisms of this ε-security criterion and highlighted the importance of accurately modelling potential adversaries and their capabilities. They emphasize that the validity of a security proof relies on aligning theoretical assumptions with real-world experimental conditions, citing the example of photon-number splitting attacks which exposed discrepancies between idealised models and practical implementations. By establishing a clear link between the trace distance between real and ideal quantum states and the probability of key failure, this research provides a robust framework for evaluating and improving the security of QKD systems.
👉 More information
🗞 Defining Security in Quantum Key Distribution
🧠 ArXiv: https://arxiv.org/abs/2509.13405