The increasing scale of future interconnected networks presents a critical vulnerability to attacks that store data now and decrypt it later, threatening the privacy of vast data streams. Nilesh Vyas from Airbus Central R and T and Konstantin Baier from Hochschule München für angewandte Wissenschaften, along with their colleagues, address this challenge by introducing the Quantum Anonymous Data Reporting (QADR) protocol. This new framework establishes both a theoretical benchmark and a high-performance architecture for scalable, quantum-resistant anonymity, crucial for future fully-connected networks. QADR achieves this by combining the security of quantum key distribution with computationally-hardened cryptography, offering a practical balance between long-term data protection and resource demands. The team demonstrates a significant performance advantage, achieving communication costs that scale linearly with network size, a dramatic improvement over existing quantum-native anonymity systems and setting a new standard for future development.
Quantum Key Distribution Collision Resolution Analysis
This study presents a detailed mathematical analysis of a collision resolution protocol, essential for managing access to shared resources in distributed systems and networks. The protocol efficiently handles simultaneous access attempts, ensuring all participants eventually succeed. Researchers used probability theory to quantify outcomes at each stage of the resolution process, applying this analysis to quantum key distribution networks. The study focuses on understanding collision occurrences and effective resolution strategies. The protocol involves participants attempting to access slots, with collisions occurring when multiple target the same slot.
The analysis centers on the collision structure, representing participant distribution across slots. The process unfolds in multiple rounds, with participants re-attempting access after each collision. Researchers modeled the likelihood of different outcomes in each round, crucial for evaluating the protocol’s efficiency. The core of the analysis is a formula calculating the probability of a specific collision structure, considering total possible outcomes, arrangement possibilities, and available slot choices. It calculates favorable outcomes, representing the specific collision structure, divided by total possible outcomes, allowing researchers to predict scenario likelihoods.
The probability of an outcome in any round depends on the previous round’s outcome, creating a conditional relationship. Researchers used conditional probability to model the entire collision resolution process over multiple rounds, accurately predicting system behavior. This protocol establishes a benchmark and high-performance architecture for scalable, post-quantum-resistant anonymity, combining quantum key distribution with a post-quantum pseudorandom function. A key innovation is a slot reservation mechanism that deliberately trades a quantifiable information leak for high performance, while maintaining strong unlinkability during data submission. Researchers formally quantified the anonymity reduction caused by this leak and explored mitigation pathways, establishing a performance benchmark with communication costs scaling as n, a significant improvement over existing alternatives that scale as n 2.
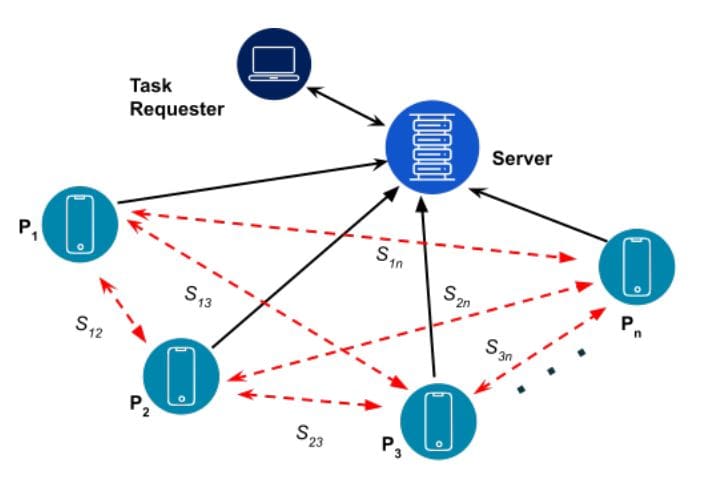
The team engineered a system where participants reserve slots for data submission, preventing an adversary from retroactively identifying individuals. This approach effectively mitigates the information leak, as all participants follow an identical procedure, eliminating distinct behavioral groups for adversarial observation. A verifiable proof ensures the integrity of the reservation process against malicious service providers, introducing a higher computational burden but delivering stronger anonymity during reservation. Researchers strategically employed a centralized, untrusted service provider to enhance scalability and simplify security analysis.
Communication complexity is reduced to n connections, with the service provider functioning as a simple, stateless aggregator performing XOR operations. This simplification allows researchers to demonstrate that the system remains secure as long as at least two participants remain honest, even against a powerful adversary compromising all but two users. They developed a detailed analytical model to assess the probability of collisions during slot reservation, analogous to the “balls and bins” problem. This model accurately calculates the probability of any sequence of collision outcomes, enabling precise evaluation of the system’s performance. Researchers also implemented simulations in Python to empirically validate the analytical model, determining the relationship between the slot-to-participant ratio and the number of rounds required for successful collision resolution. Recognizing the limitations of existing solutions, the team created a hybrid approach combining the strengths of both quantum and classical cryptography, achieving a balance between robust security and practical scalability. At the core of QADR is the use of quantum key distribution to establish secure, shared keys between participants, forming a foundation of trust. These keys are then used to seed a quantum-secure pseudorandom function, extending the key’s utility for encrypting larger data volumes.
Experiments demonstrate that commercial quantum key distribution systems can currently achieve key rates of kilobytes per second, sufficient for many applications involving small data payloads like traffic alerts or environmental sensor readings. For larger data transfers, the quantum-secure pseudorandom function provides a practical cryptographic extension, though the overall security then relies on the computational hardness of the chosen function against quantum attacks. The protocol’s architecture involves participants submitting masked data to a server, which aggregates the information before forwarding it to the task requester. A key achievement is the communication cost, which scales as n, a significant improvement over alternative systems that scale as n 2.
This improved scalability is crucial for handling the massive data streams expected from future fully-connected networks. Researchers formally analyzed the protocol, proving its performance advantage and quantifying any potential information leaks during the anonymous slot reservation phase, while also outlining pathways to mitigate these leaks at the cost of performance. The research establishes a benchmark for future quantum-resistant anonymity systems, demonstrating a viable path toward protecting sensitive data in an era of increasingly powerful computing capabilities. Recognizing the vulnerability of these networks to attacks that prioritize data collection now and decryption later, the team developed a hybrid approach combining post-quantum cryptography with quantum key distribution. This allows for scalable, privacy-preserving data transmission while establishing a benchmark.
👉 More information
🗞 QADR: A Scalable, Quantum-Resistant Protocol for Anonymous Data Reporting
🧠 ArXiv: https://arxiv.org/abs/2511.15272