Quantum key distribution promises unconditionally secure communication, but achieving this over long distances remains a significant challenge. Frederik Brooke Barnes, Roberto G. Pousa, and Christopher L. Morrison, working at Heriot-Watt University and the University of Strathclyde with colleagues including Zhe Xian Koong, Joseph Ho, and Francesco Graffitti, now demonstrate a substantial step forward in this field. The team implements a sophisticated decoy-state quantum key distribution scheme using a practical, telecom-band single-photon source, and importantly, they calculate secure key rates accounting for real-world imperfections. This approach achieves positive secret key rates over 227 kilometres of fibre, representing a tenfold improvement in loss tolerance compared to traditional methods and paving the way for more robust, long-distance quantum communication networks.
Record Distance Quantum Key Distribution Achieved
Scientists have achieved a significant breakthrough in secure communication by demonstrating quantum key distribution (QKD) over a record distance of 227 kilometres. This achievement utilises a decoy-state protocol and a frequency-converted telecom single-photon source, enabling secure communication through standard optical fibre. The team actively mitigates photon number splitting attacks, a critical vulnerability in QKD systems, and optimises source and detection parameters to improve key generation rates. This demonstrated system represents a substantial step towards building practical, long-distance quantum communication networks, offering enhanced security compared to classical cryptographic methods.
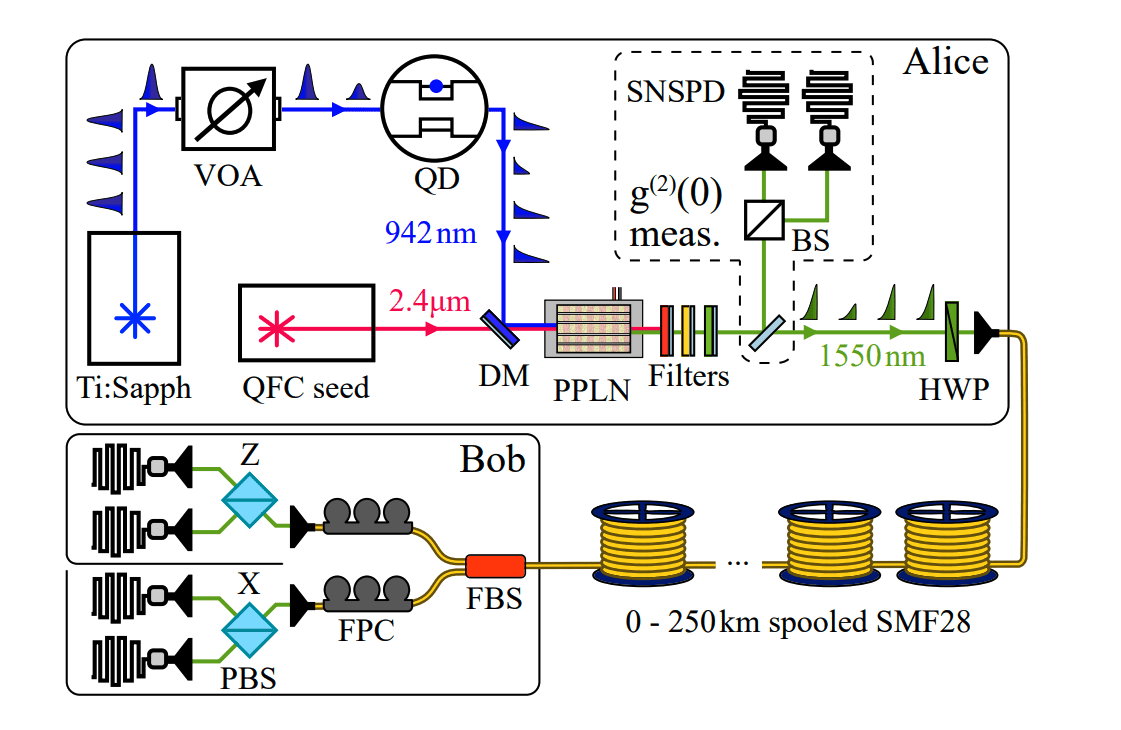
The team implements a decoy-state QKD scheme using a telecom C-band single-photon emitter. Decoy states are created by carefully controlling the optical excitation of the quantum emitter, modulating the distribution of photons emitted. Detailed analysis, based on established security proofs, allows calculation of secret key rates, accounting for the practical limitations of real-world systems. This enables the demonstration of positive secret key rates over 227 kilometres of optical fibre, representing a significant improvement in loss tolerance compared to non-decoy schemes and broadening the potential applications of single-photon sources.
Decoy-State QKD and Quantum Dot Sources
Research in quantum key distribution (QKD) and single-photon sources, particularly those based on semiconductor quantum dots, is rapidly advancing. A central theme is improving the security and practicality of QKD using the decoy-state method, which addresses vulnerabilities in earlier protocols by sending weak signals alongside the main communication signal to detect eavesdropping attempts. This research also focuses on tightening security bounds and rigorously analysing system vulnerabilities to ensure truly secure key exchange.
Quantum dots are considered promising candidates for generating high-quality single photons due to their discrete energy levels and potential for on-demand emission. A major focus is achieving truly single-photon emission, characterised by sub-Poissonian statistics, and ensuring that emitted photons are indistinguishable, a critical requirement for interference-based QKD protocols. Researchers are exploring ways to control quantum dot emission properties, such as rate, polarisation, and timing, to optimise performance and are developing scalable fabrication techniques to integrate quantum dots into practical devices.
Many studies focus on implementing QKD over optical fibre, the most practical medium for long-distance communication, while others explore free-space QKD, which offers higher data rates but is susceptible to atmospheric disturbances. Extending the range of QKD systems is a major challenge, limited by photon loss in the fibre, and increasing the key generation rate is crucial for practical applications. Several experimental demonstrations showcase QKD systems performing in realistic scenarios, integrating all components and addressing the limiting factor of single-photon detector efficiency.
Advanced techniques include developing triggered single-photon sources, where emission is controlled by an external stimulus, and converting the wavelength of single photons to the telecom band to minimise fibre loss. Using entangled photon pairs can enhance security and performance, and researchers are exploring various encoding techniques, such as polarisation and time-bin encoding. Variations of decoy-state protocols are being developed to address specific vulnerabilities and improve performance, and integrating quantum dots into waveguides improves light collection efficiency. Developing QKD systems that operate at room temperature is crucial for practical deployment, and research is exploring novel materials, such as hexagonal boron nitride, as potential single-photon emitters.
The overall trend is towards building practical, real-world QKD systems, with quantum dots emerging as a leading technology for generating the necessary single photons. There is a growing emphasis on integrating all system components and optimising their performance, alongside ongoing research refining QKD protocols and tightening security bounds. This research is paving the way for secure communication networks based on the principles of quantum mechanics.
Decoy States Extend QKD Distance Significantly
Scientists have demonstrated a significant advance in quantum key distribution (QKD) by successfully implementing a decoy-state protocol using a single-photon source operating at a telecommunications wavelength. This achievement enables positive secret key rates over 227 kilometres of fibre, representing a substantial improvement in distance compared to QKD systems that do not employ decoy states. This relaxes the demanding requirements for single-photon purity, broadening the potential for practical, long-distance quantum communication networks.
The team’s approach involves modulating the excitation of the single-photon source to create decoy states, a technique that enhances security and extends the feasible transmission distance. Results show that the performance of this imperfect source closely approaches that of an ideal single-photon source, demonstrating the effectiveness of the decoy-state method in mitigating the impact of source imperfections. This work expands the scope of quantum dot sources, positioning them as viable components for future quantum networks and practical QKD systems.
👉 More information
🗞 Decoy-state quantum key distribution over 227 km with a frequency-converted telecom single-photon source
🧠 ArXiv: https://arxiv.org/abs/2512.05101