The pursuit of a secure quantum internet demands new methods for transmitting and processing information, and researchers are now demonstrating a significant step forward with a novel approach to secure computation. Lev Stambler from the University of Maryland, College Park, and NeverLocal Ltd, alongside colleagues, introduces Verifiable One-Time Programs, a technique that enables single-round Open Secure Computation. This breakthrough unlocks possibilities for applications ranging from secure auctions to building blocks for consensus protocols and even privacy-preserving data aggregation, all without requiring prior registration. Crucially, the team achieves this using minimal quantum resources, single-qubit states, alongside established cryptographic techniques, paving the way for implementation with potentially near-term quantum technology.
The security of the system rests on carefully constructed arguments, demonstrating that an adversary cannot distinguish the real computation from an ideal scenario. The core of the security proof demonstrates that the system’s execution is indistinguishable from an ideal functionality, where a trusted party would compute the function on the inputs and provide the result.
This is achieved through a series of hybrid arguments, where the system is modified step-by-step, and each modification is shown not to alter the indistinguishability between the real and ideal worlds. Crucially, the system accounts for the possibility of compromised parties, ensuring security even in the presence of malicious actors. The approach strategically balances quantum simplicity with classical computation, addressing the physical limitations of current technology. These programs output both the share itself and a proof of its validity, allowing the receiver to randomly select a portion of them for verification. By checking the validity of these opened programs, the receiver gains confidence in the integrity of the remaining unopened programs, enabling secure data recovery. The core of the system focuses on minimizing quantum resources, employing single-qubit BB84-like states for the underlying One-Time Programs while leveraging classical cryptography for the remaining components. The team constructed Verifiable One-Time Programs by making both garbled circuits and one-time memories verifiable, utilizing non-interactive zero-knowledge proofs to confirm correct garbling and a novel approach to verifiable one-time memories.
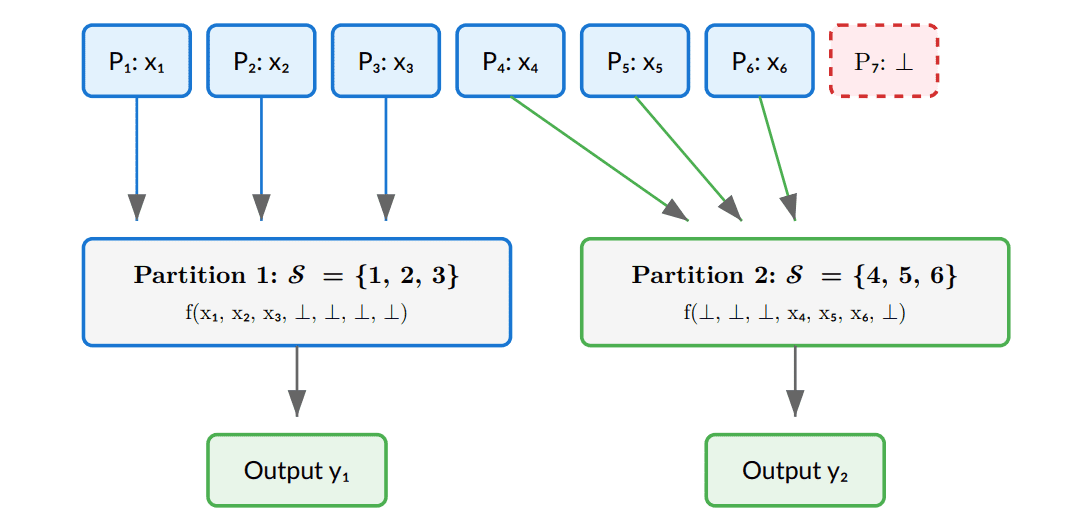
These memories employ a cut-and-choose technique combined with secret sharing, generating multiple secret shares for each data element. Each share is placed within a single-bit One-Time Program, outputting both the share itself and a proof of its validity. The receiver randomly selects a portion of these programs to verify the shares and proofs, ensuring with high probability the integrity of the remaining unopened programs. Within this system, the receiving party can adaptively partition inputs from sending parties into disjoint groups, computing a function on each group. This formulation safeguards against partitioning attacks where the receiver might selectively include inputs in different computations. Researchers constructed verifiable one-time programs using single-qubit states and classical cryptographic techniques, then leveraged these programs, alongside a multi-key homomorphic encryption scheme, to build open secure computation. This advancement enables several applications, including single-round sealed-bid auctions, atomic proposals for consensus protocols, and differentially private statistical aggregation without requiring prior registration of participants. The significance of this research lies in its potential to simplify distributed protocols, allowing a single party to execute the entire protocol while maintaining security.
This is particularly useful in scenarios where a cloud service is trusted to run computations but not to access sensitive input data. While the current construction relies on a common reference string, this does not directly impact the protocol’s execution. Future research directions include exploring constructions without this requirement, improving the efficiency of the programs, and enhancing their fault tolerance in noisy real-world environments. Further investigation will also explore extending these concepts to fully quantum computational settings and identifying additional applications that can benefit from the “open” nature of this new form of secure computation.
👉 More information
🗞 New Quantum Internet Applications via Verifiable One-Time Programs
🧠 ArXiv: https://arxiv.org/abs/2509.22290