Crypto-agility has emerged as a critical concept for ensuring robust cybersecurity in today’s rapidly evolving digital landscape. As emerging technologies like quantum computing pose significant threats to traditional cryptographic methods, there is an urgent need for new approaches to protect sensitive information.
Standards and guidelines, such as those provided by NIST, are pivotal in facilitating the transition to more secure algorithms and key lengths without disrupting existing systems. Additionally, frameworks like zero-trust architecture enhance security by verifying every access request, adding an extra layer of protection. To effectively implement these changes, organizations can utilize maturity models that assess their readiness for crypto-agility, ensuring they are well-prepared to adopt new cryptographic standards and maintain secure operations in the face of future challenges.
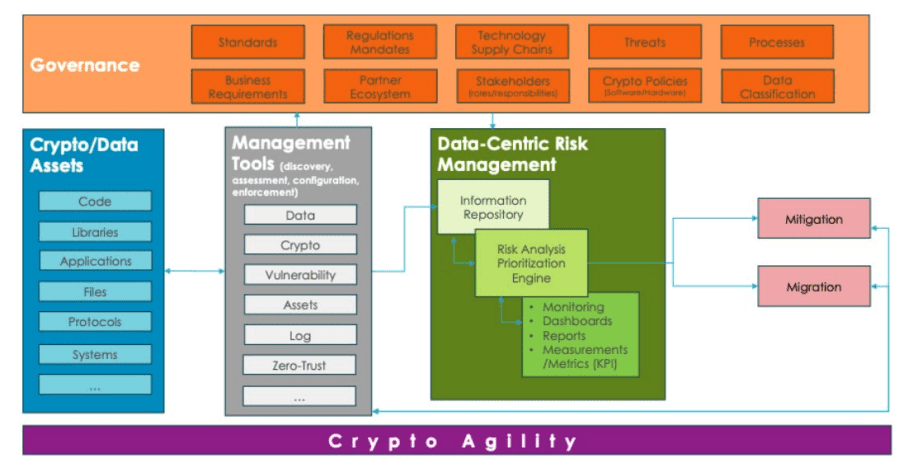
The Crypto Agility Maturity Model (CAMM), developed by NIST, is a strategic framework designed to help organizations adapt their cryptographic practices in response to evolving technologies, particularly addressing the looming threat of quantum computing. CAMM focuses on four key areas:
- Inventorying and Managing Cryptographic Assets: This involves identifying and cataloging all cryptographic tools and systems within an organization. Effective management ensures these assets are secure, up-to-date, and compliant with standards like FIPS 140-2 and SP 800-57, which are crucial for sectors requiring high trust levels, such as government and finance.
Integrating New Methods: CAMM facilitates the incorporation of new cryptographic techniques, such as post-quantum cryptography (PQC), into existing systems without necessitating a complete overhaul. This approach allows organizations to enhance security incrementally while maintaining functionality.
Monitoring for Vulnerabilities: Continuous monitoring is essential for detecting emerging threats and vulnerabilities promptly. This proactive measure enables timely mitigation strategies, reducing the risk of breaches.
Planning Transitions: CAMM emphasizes the importance of having a roadmap for transitioning cryptographic practices. This involves planning ahead to replace outdated systems or algorithms before they become vulnerable, ensuring a smooth and secure transition process.
CAMM is noted for its flexibility, allowing organizations to assess their readiness and plan improvements according to their specific needs and resources. By providing a structured approach, CAMM bridges the gap between legacy systems and newer technologies, making upgrades cost-effective and promoting preparedness and adaptability in a rapidly changing technological landscape.
More information
External Link: Click Here For More




