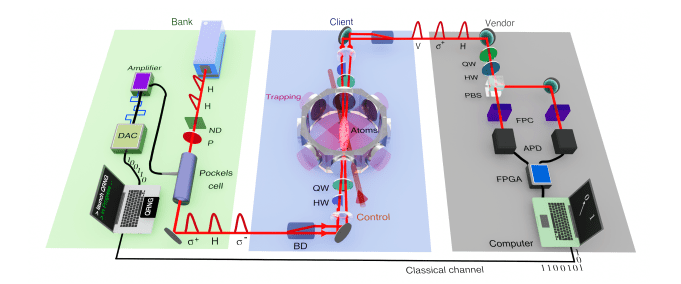
On March 31, 2025, researchers published new research on optical quantum memory, detailing the first successful integration of optical quantum memory into a cryptography protocol. This breakthrough involved implementing Wiesner’s unforgeable money primitive with a storage step, marking a significant advancement in secure communication and scalable quantum networks.
The research demonstrates a cryptography protocol incorporating an intermediate memory layer, specifically implementing Wiesner’s unforgeable money primitive with a storage step using polarization encoding of weak coherent states and a high-efficiency cold-atom-based memory. The protocol validates secure storage and buffering capabilities, showcasing advancements in optical memories for future technologies and network functionalities.
Secure communication has become a cornerstone of modern society in the digital age. From safeguarding financial transactions to protecting sensitive data, ensuring the integrity of information is paramount. Quantum key distribution (QKD) offers a promising solution by leveraging the principles of quantum mechanics to enable ultra-secure communication. However, as with any emerging technology, challenges remain in addressing potential vulnerabilities, particularly those related to cloning attacks.
The Threat of Cloning Attacks
Quantum money, a form of quantum information, relies on the no-cloning theorem, which states that an unknown quantum state cannot be perfectly replicated. This property ensures that quantum money is inherently secure against counterfeiting. However, practical implementations must account for imperfect cloning attempts, where adversaries may introduce noise or errors to bypass security measures.
Researchers have developed sophisticated methods to evaluate these threats, employing mathematical frameworks such as semidefinite programming (SDP) to model and optimize potential attacks. SDP is a powerful tool in quantum information theory, enabling the formulation of complex optimization problems that help identify the most effective counterfeiting strategies an adversary might employ.
Optimizing Security with Mathematics
In the context of quantum money, SDP determines the optimal cloning strategy that minimizes the noise introduced while adhering to specific constraints. These constraints include maintaining trace-preserving maps and ensuring the resulting operators are positive semidefinite, which are essential for the physical realizability of the attack.
By casting the problem as an SDP, researchers can leverage computational tools like the SDPT3 solver within MATLAB to find solutions efficiently. This approach not only helps in identifying potential vulnerabilities but also ensures that security protocols are robust against a wide range of attacks, including those targeting multiple quantum states simultaneously.
The application of SDP in securing quantum money has significant implications for the future of quantum communication. By establishing strong duality in optimization problems, researchers can guarantee that the derived solutions are optimal and reliable. This confidence is crucial as we move towards implementing large-scale quantum networks.
Moreover, understanding and mitigating cloning attacks through advanced mathematical techniques underscores the importance of interdisciplinary research. It highlights how insights from quantum mechanics, computer science, and applied mathematics converge to address real-world security challenges.
As we continue to explore the frontiers of quantum technology, ensuring the security of quantum money remains a critical objective. By harnessing the power of semidefinite programming and computational tools like SDPT3, researchers are paving the way for more robust and reliable quantum communication systems. These advancements not only enhance our ability to protect sensitive information but also foster trust in the emerging quantum landscape.
With ongoing research and collaboration across disciplines, the future of secure communication looks promising, offering a blend of theoretical rigor and practical innovation that will undoubtedly shape the next generation of digital security.
👉 More information
Quantum cryptography integrating an optical quantum memory
🧠 DOI: https://doi.org/10.48550/arXiv.2504.00094