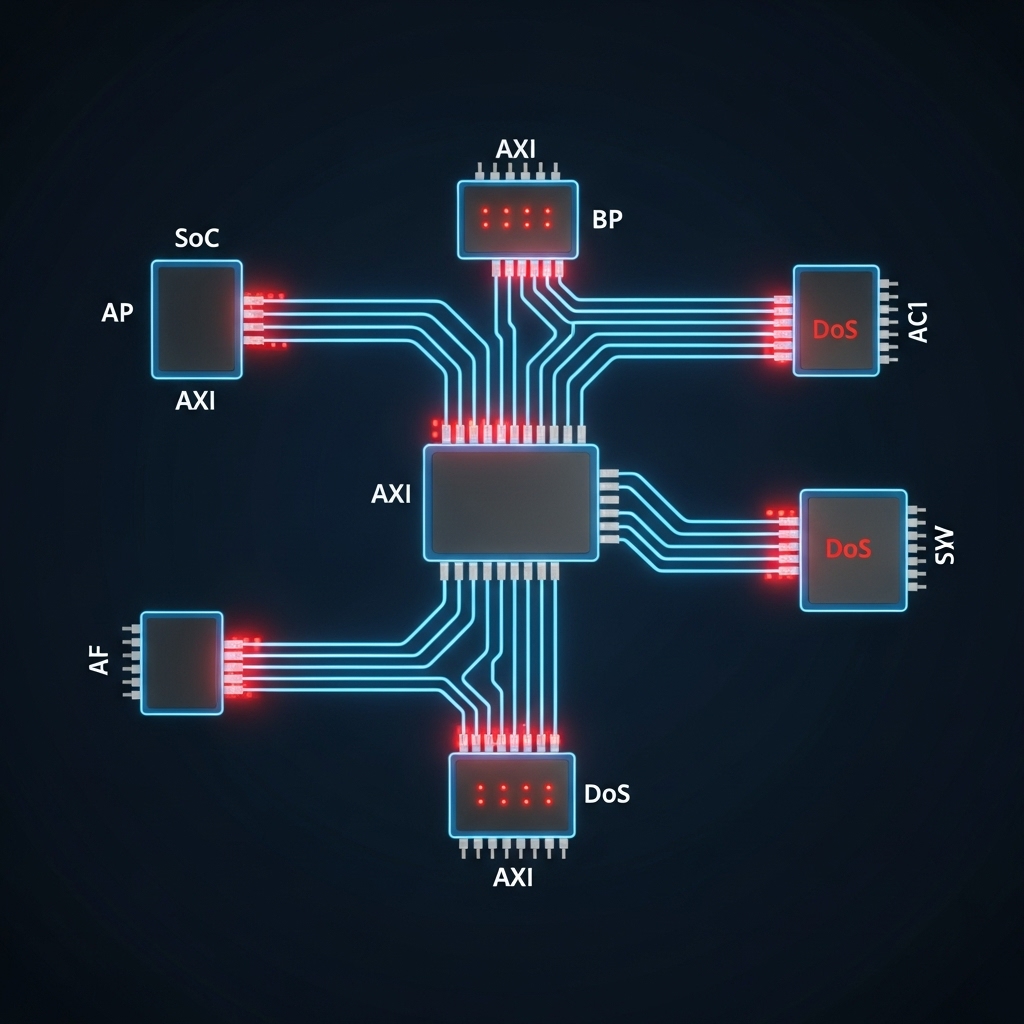
A growing threat to modern Systems-on-Chip (SoC) security stems from vulnerabilities within the Advanced eXtensible Interface (AXI) protocol, potentially leading to disruptive denial-of-service attacks. Researchers Wadid Foudhaili (Universit at zu L ubeck), Aykut Rencber (TU Braunschweig), and Anouar Nechi (Universit at zu L ubeck), et al., address this critical issue with the development of an Intelligent Hardware Monitoring System (IMS) for real-time detection of AXI protocol violations. Unlike existing countermeasures, IMS employs neural networks to perform dedicated, real-time protocol semantic analysis, achieving 98.7% detection accuracy with minimal latency overhead, a significant advancement for safeguarding resource-constrained edge environments. Their work, detailed in this paper, demonstrates the feasibility of lightweight, in-hardware security monitoring, paving the way for more robust and secure SoC designs.
AXI Protocol Attack Detection via Machine Learning
Scientists have demonstrated a novel intelligent hardware monitoring system (IMS) designed to detect and mitigate denial-of-service (DoS) attacks targeting the Advanced eXtensible Interface (AXI) protocol within modern Systems-on-Chip (SoCs). The research addresses a critical vulnerability where malicious or malfunctioning components can disrupt communication, causing partial or complete system failure through protocol-level attacks. Unlike existing countermeasures that focus on access control, this work introduces a dedicated real-time protocol semantic analysis leveraging machine learning to identify subtle violations undetectable by conventional methods. The team achieved this by developing a hardware module that employs neural networks for high detection accuracy, effectively safeguarding SoC functionality against sophisticated threats.
For model training, researchers systematically generated DoS attacks by manipulating AXI header fields and performing malicious operations, meticulously recording AXI transactions to create a comprehensive training dataset. Subsequently, they deployed a quantization-optimized neural network, achieving an impressive 98.7% detection accuracy while maintaining a latency overhead of less than 3% and a throughput exceeding 2.5 million inferences per second. This performance benchmark signifies a substantial advancement in real-time security monitoring capabilities for complex systems. The IMS was then seamlessly integrated into a RISC-V SoC as a memory-mapped IP core, allowing for direct monitoring of the AXI bus and demonstrating its practical applicability within a standard SoC architecture.
To validate the feasibility of this approach for resource-constrained edge environments, the team implemented the IMS on a Zynq UltraScale+ MPSoC ZCU104 board. Results showed a remarkably small hardware footprint, consuming only 9.04% of look-up-tables (LUTs), 0.23% of DSP slices, and 0.70% of flip-flops, with a negligible impact on the overall design’s achievable frequency. This minimal overhead confirms the viability of lightweight, high-performance security monitoring even in devices with limited resources. The researchers have also made their AXI bus header attack detection dataset publicly available, fostering reproducibility and encouraging further research in protocol-level SoC security.
This breakthrough establishes a new paradigm for SoC security, moving beyond traditional access control to encompass real-time protocol semantic analysis. The work opens avenues for proactive threat detection and mitigation, enhancing the resilience of critical systems against increasingly sophisticated attacks. By demonstrating a highly accurate and efficient hardware implementation, the study paves the way for integrating robust security monitoring into future SoC designs, particularly in applications demanding high reliability and availability, such as automotive systems and industrial control.
AXI Violation Detection Using Neural Networks
Scientists engineered an intelligent hardware monitoring system (IMS) for real-time detection of Advanced eXtensible Interface (AXI) protocol violations, addressing security vulnerabilities in modern Systems-on-Chip (SoCs). The research team developed a hardware module leveraging neural networks to achieve high detection accuracy and combat potential denial-of-service (DoS) attacks, a significant improvement over existing countermeasures lacking dedicated real-time protocol semantic analysis. To begin, researchers constructed a comprehensive training dataset by recording AXI transactions under both normal and malicious conditions using a Chipyard Platform for a RISC-V SoC. The study pioneered a dual-mode data collection strategy, capturing 16,383 legitimate transactions during standard Linux OS runtime to establish a baseline of typical system behaviour across all five AXI channels: Write Address (AW), Write Data (W), Write Response (B), Read Address (AR), and Read Data (R).
Subsequently, the team systematically generated 3,242 attack samples representing three critical scenarios: illegal burst configurations exceeding a length of 15, transaction ID exploits using duplicate ARID values, and quality of service (QoS) signal flooding with a saturation value of 0xF, all designed to induce DoS conditions. These malicious operations were carefully synthesised to mimic the behaviour of malfunctioning or untrustworthy IP cores disrupting bus operation. Following dataset creation, scientists applied feature engineering methods to identify the most representative characteristics for model training. The approach involved signal encoding and correlation analysis, followed by Principal Component Analysis (PCA)-based feature compression and hardware-aware feature selection to reduce dimensionality and optimise performance.
A quantization-optimized neural network was then deployed, achieving 98.7% detection accuracy with latency overhead of less than or equal to 3% and a throughput exceeding 2.5 million inferences per second. Researchers subsequently integrated the IMS into the RISC-V SoC as a memory-mapped IP core, monitoring the AXI bus and demonstrating a small hardware footprint, 9.04% look-up-tables (LUTs), 0.23% DSP slices, and 0.70% flip-flops, with negligible impact on the overall design’s achievable frequency. Implementation on a Zynq UltraScale+ MPSoC ZCU104 board confirmed the feasibility of lightweight, security monitoring for resource-constrained edge environments, paving the way for ASIC integration and enhanced SoC security.
AXI Violation Detection via Neural Networks is a
Scientists have demonstrated a novel intelligent hardware monitoring system (IMS) for real-time detection of Advanced eXtensible Interface (AXI) protocol violations in Systems-on-Chip (SoCs). This IMS utilises neural networks to identify malicious operations that could lead to denial-of-service attacks, addressing a significant security vulnerability in modern SoCs. Researchers constructed a dedicated dataset of both normal and malicious AXI traffic, captured from a RISC-V SoC on a Xilinx ZCU104 FPGA platform, to train the machine learning model. The resulting optimised model achieves high detection accuracy, reaching up to 99.11% AUC-ROC, alongside robust performance in precision, recall, and F1 metrics.
Importantly, the implemented IMS exhibits a small hardware footprint, utilising only 9.04% look-up-tables, 0.23% DSP slices, and 0.70% flip-flops, and introduces minimal latency (1.566ms) with a throughput exceeding 2.5 million inferences per second. This work establishes the feasibility of lightweight, protocol-aware security monitoring for resource-constrained edge devices. The authors acknowledge that their current work primarily focuses on denial-of-service attacks and further research is needed to broaden attack coverage to encompass additional AXI channels and violation types. Future investigations will explore alternative machine learning architectures, such as LSTM and GNN, to enhance zero-day attack detection capabilities. Integration with existing SoC security frameworks, including firewalls and hypervisors, is also planned to create a layered, defense-in-depth protection strategy, alongside ASIC integration utilising advanced technology libraries.
👉 More information
🗞 IMS: Intelligent Hardware Monitoring System for Secure SoCs
🧠 ArXiv: https://arxiv.org/abs/2601.11447