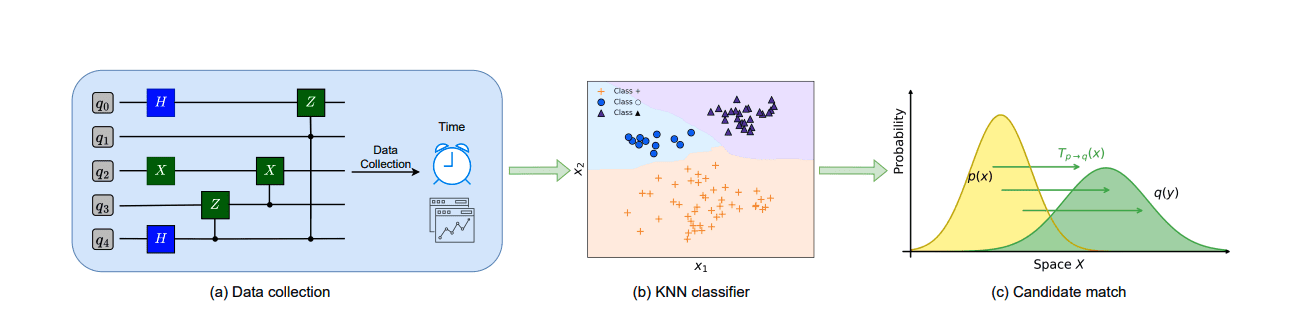
Circuit simulators are increasingly vital tools as computing advances, bridging the gap between design and available hardware, yet they introduce new security vulnerabilities. Ben Dong, Hui Feng, and Qian Wang, all from the University of California, Merced, demonstrate a novel timing side-channel attack that targets these cloud-based simulators, revealing sensitive information about user designs. The team shows that a malicious process, running alongside legitimate simulations, can observe subtle variations in execution timing to identify the circuits being simulated. Through systematic analysis using the QASMBench benchmark suite, they demonstrate that these timing patterns exhibit circuit-dependent characteristics, allowing an adversary to accurately infer circuit identities with up to 99. 9% success. This research highlights previously unknown risks in simulation environments and underscores the need for improved isolation mechanisms to safeguard user confidentiality.
Quantum Side-Channel Attacks and Vulnerabilities
This document presents a comprehensive exploration of security vulnerabilities in quantum computing, focusing specifically on side-channel attacks. It argues that quantum computers, despite their cryptographic promise, are susceptible to the same kinds of side-channel attacks as classical computers, and potentially even more vulnerable due to the delicate nature of quantum states. The research covers vulnerabilities in quantum hardware, software, and control systems, as well as the application of machine learning for both attack and defense. The study details how attackers can extract information from a quantum computer without directly breaking the quantum algorithm itself, examining techniques like timing attacks, power analysis, and electromagnetic radiation analysis.
It also explores vulnerabilities in the software used to program and control quantum computers, such as the potential for code injection and data leakage. Machine learning plays a dual role, enhancing the effectiveness of side-channel attacks and providing tools for detecting and mitigating these threats. The research also investigates hardware and software countermeasures, including shielding, code obfuscation, and trusted execution environments. This work demonstrates that security is a fundamental challenge that must be addressed from the beginning of quantum computer design and development, requiring a holistic approach encompassing hardware, software, and control systems. New security paradigms are needed, and continued research and development are essential to identify and mitigate vulnerabilities. The findings have significant implications for quantum cryptography, as side-channel attacks could compromise the implementation of quantum key distribution and undermine its security.
Timing Attacks Reveal Simulator Vulnerabilities
Scientists have developed a methodology to assess security vulnerabilities in quantum circuit simulators, demonstrating a timing side-channel attack that extracts sensitive information from concurrent circuit executions. The study employed the QASMBench benchmark suite to systematically analyze simulator behavior, executing both small-scale and medium-scale circuits on a high-performance workstation. During circuit execution, the team meticulously collected runtime metrics, capturing fine-grained performance characteristics. The research involved profiling timing and memory characteristics across a diverse range of circuit executions, enabling the identification of circuit-dependent patterns within the timing profiles.
Scientists leveraged pattern recognition techniques to classify these profiles, successfully inferring circuit identities and demonstrating a potential compromise of user confidentiality. Results show the methodology achieves high identification rates for quantum circuits, highlighting the effectiveness of the timing side-channel attack. This work pioneers a new approach to security assessment in quantum simulation, revealing previously unexplored risks and emphasizing the need for stronger isolation mechanisms to protect user workloads and proprietary algorithms. The study’s findings have significant implications for domains such as quantum chemistry, finance, and cryptography.
Timing Reveals Quantum Circuit Structure
This research demonstrates a novel timing side-channel attack targeting cloud-based quantum circuit simulators. By carefully analyzing execution timing and memory characteristics, the team successfully extracted sensitive information about concurrently running circuits, revealing structural properties and enabling accurate identification. The work establishes that even seemingly innocuous timing variations can leak data, posing a previously unrecognised security risk within simulation environments. Across a suite of circuits, the researchers achieved high accuracy in inferring qubit and gate counts, and ultimately, identifying the circuits themselves.
Notably, the team found that medium-scale circuits were particularly vulnerable, exhibiting uniquely identifiable timing signatures, a counterintuitive finding that highlights increasing risks with larger quantum workloads. This suggests that as quantum simulations grow in complexity, the potential for information leakage through timing attacks also increases, raising significant concerns for confidentiality and competitive intelligence. The authors recommend exploring scaling these experiments to larger circuits and more advanced simulators, as well as integrating adversarial machine learning models to enhance attack capabilities. They also recommend investigating practical defenses, such as randomized timing and workload batching, to mitigate these risks and quantify their performance impact. Safeguarding quantum simulators against timing side-channels is, therefore, a crucial step towards establishing trustworthy quantum computing in both academic and commercial settings.
👉 More information
🗞 Exploiting Timing Side-Channels in Quantum Circuits Simulation Via ML-Based Methods
🧠 ArXiv: https://arxiv.org/abs/2509.12535