The proliferation of social media has created unprecedented opportunities for influence, but also raises concerns about covert communication, a topic Eric Filiol, an independent researcher based in Paris, France, and colleagues explore in a new study. They investigate how techniques used to manage large online communities can be repurposed to transmit substantial amounts of encrypted information to select recipients, effectively creating a hidden communication channel. This research demonstrates that coordinated networks of automated accounts, or ‘sock puppets’, move beyond simple influence operations and enable the discreet transfer of data, potentially up to tens of megabytes in volume. By redefining the very nature of communication, this work suggests traditional methods of surveillance and disruption, such as eavesdropping and jamming, become increasingly ineffective against such sophisticated covert networks.
AI, Disinformation and Threats to Democracy
This document presents a comprehensive investigation into the world of digital manipulation, disinformation, and the tools used to influence public opinion, elections, and geopolitical events. It argues that the increasing sophistication of these tools, including social media manipulation, AI-driven bots, and advanced data analytics, poses a significant threat to democratic processes and individual autonomy, eroding trust in information and making it increasingly difficult to distinguish truth from falsehood in the digital age. The document covers a vast range of interconnected topics, examining how social media platforms are exploited to spread false narratives, propaganda, and divisive content. Specific examples of campaigns are detailed, including those originating in China, the operations of a firm known as Team Jorge offering influence operations, the Cambridge Analytica data scandal, and the use of platforms like NationBuilder and Ripon for political campaigning and potential manipulation.
The research also explores the technical tools employed in these campaigns, such as bots and automated accounts used to amplify messages, AI-driven content generation creating realistic but false content, data analytics and microtargeting identifying and targeting specific individuals, and persona management software used by governments and organizations to create and manage fake online identities. The document further highlights the role of governments in using these techniques for espionage, influence operations, and political interference. While primarily focused on the threats, the document also touches on potential countermeasures, including warrant canaries signaling government data requests, dead man’s switches releasing information upon an individual’s incapacitation, environmental key generation creating cryptographic keys from environmental noise, and frequency hopping for secure communication. The research delves into the use of hypergraphs as a more sophisticated way to model complex social networks and identify communities, and raises important ethical and legal questions about the use of these technologies and the need for regulation.
Social Network Cloaking of Encrypted Communication
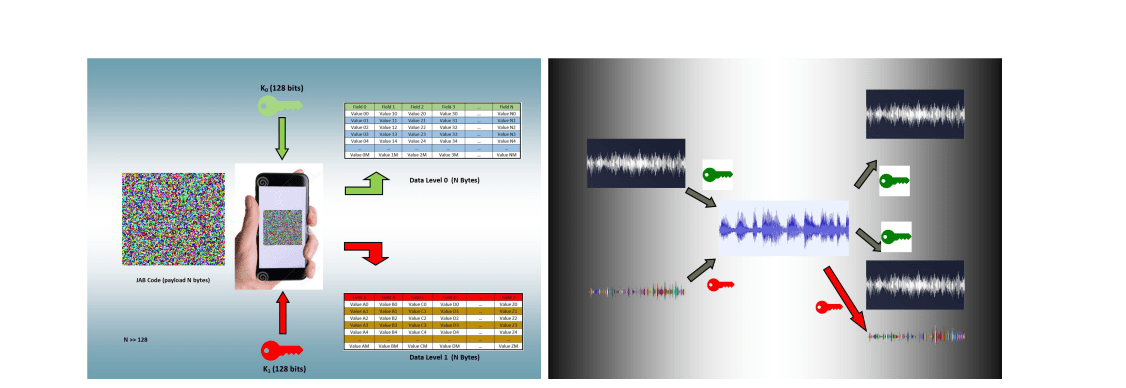
Researchers pioneered a communication system, termed CCC, that conceals encrypted information within the structure of social networks, moving beyond reliance on a single communication channel. This work centers on the manipulation of online communities through the creation and organization of numerous automated accounts, termed ‘sock puppets’, to disseminate encrypted data. The core innovation lies in leveraging these communities to encode and transmit information, effectively redefining communication such that traditional eavesdropping, interception, and jamming techniques become ineffective. The team engineered a system where encrypted data is embedded within the connections and activity of these artificially constructed communities.
The method involves establishing a network of accounts and dynamically reconfiguring the links between them, creating a constantly shifting structure that defies conventional community detection algorithms. This dynamic reconfiguration prevents the application of methods reliant on the stability of social network structures, which typically analyze the density of connections to identify communities. The system’s security relies on a two-fold cryptographic approach, employing a highly non-linear combiner of non-linear feedback shift registers that has proven resistant to known attacks, including correlation and algebraic attacks. Furthermore, the encryption enforces non-trivial deniable encryption, adding another layer of security.
The team explored the theoretical limits of community creation, noting that the number of possible communities within a network of nv elements is defined by Bell’s number, a computationally intractable value even for relatively small networks. Considering the vast number of attributes present in real-world social networks, the potential number of community configurations becomes astronomically high, further enhancing the system’s security. Future work focuses on enhancing the system’s performance and security, including weighting nodes and edges to improve encoding efficiency, incorporating existing real user profiles to add noise and obfuscation, and increasing the system’s inconspicuousness by utilizing environmental data. The team also intends to formally assess the cryptographic security of the CCC technology and explore potential commercial applications.
Sock Puppet Networks Enable Covert Communication
This research demonstrates a novel communication technique, the Community Covert Communication Technique (CCCT), which enables the secure transmission of multi-level encrypted information to a limited number of actors using a network of managed online communities. The work addresses a growing trend in influence operations, where automated systems generate and manage large numbers of fake online profiles, known as sock puppets, to manipulate public opinion and disseminate information. Researchers identified and analyzed several key software platforms used in these operations, including NTrepid’s software utilized in Operation OEV, which provides licenses for fifty operators, each controlling ten fake accounts. The study details how these systems function by generating and managing armies of sock puppet accounts in real time, enabling micro-targeting and the creation of viral content across multiple social media platforms, including Facebook, Twitter, LinkedIn, and Telegram.
A core principle of these operations is the ability to manage and synchronize multiple communities across different social networks through a single application programming interface (API), effectively creating a meta-network where each social network functions as a subset of interconnected communities. Researchers emphasize that the content of profiles and their communications are as crucial as the connections between them, with the density of these connections defining the strength of a community. The CCCT technique leverages this understanding of community dynamics to transmit information securely. The research highlights the importance of thinking in terms of communities when designing covert communication strategies. Analysis of existing software, such as Ripon used in the Cambridge Analytica scandal, reveals the capabilities of these systems for generating and managing fake accounts on a large scale. The work establishes a foundation for understanding and potentially countering the increasingly sophisticated techniques employed in modern influence operations by focusing on the underlying principles of community management and covert communication.
Covert Communication via Distributed Online Communities
This research demonstrates a novel approach to secure communication, termed Covert Communication via Communities, which utilizes social network-based influence operations to transmit encrypted information. The team successfully showed that large volumes of data can be disseminated to a limited number of recipients through strategically managed online communities, effectively creating a communication channel resistant to traditional interception and jamming techniques. This method relies on the creation and organization of numerous automated online personas, or “sock puppets”, to establish a robust and concealed communication network. The core achievement lies in redefining the concept of communication security by moving away from single-channel reliance and embracing a distributed, community-based system. The encryption algorithm employed combines a highly non-linear structure with deniable encryption, providing a two-fold security measure against known attacks.
👉 More information
🗞 Community Covert Communication – Dynamic Mass Covert Communication Through Social Media
🧠 ArXiv: https://arxiv.org/abs/2509.17508